 The Evolving Craft of Intelligence [Version 3.1]
The Evolving Craft of Intelligence [Version 3.1]
Robert David Steele
There is little desire in the developed intelligence nations to see the craft of intelligence evolve in line with the revolutions in information technology and globalization. Indeed, it can safely be said that most leaders with access to intelligence services do not value them—they are much more influenced by networks of influence and ideology that demand the status quo. Where intelligence is used at all it is generally to confirm pre-existing policy positions rather than what governing elites need to know. (Davis 1986, Garland 2012, Pillar 2011, Treverton 1986).
Ada Bozeman has written:
(There is a need) to recognize that just as the essence of knowledge is not as split up into academic disciplines as it is in our academic universe, so can intelligence not be set apart from statecraft and society, or subdivided into elements…such as analysis and estimates, counterintelligence, clandestine collection, covert action, and so forth. Rather … intelligence is a scheme of things entire. (Bozeman 1998: 177):[1]
What can be observed within both the closed intelligence communities and open academic, civil society, commerce, government at all levels, law enforcement, media, military, and non-governmental/non-profit (hereafter the “eight communities”) is a failure to comprehend the shift in the nature and reliability of their unwittingly shared sources and methods; the Earth (reality), and the mix of humanity, culture and technology.
Intelligence—the art of forecasting, warning, and holistic evaluation of cause and effect—has generally focused in the past on the identification and evaluation of grave threats and in supporting the judgment of executive agencies and political leaders with respect to those threats (Iraq and Afghanistan are two such recent incidents, and Iran is likely to become the next incident of its type).
Since 1988 I have sought to generate a paradigmatic shift in the understanding of intelligence so as to refocus it on holistic analytics and opportunities as well as the expansion of the craft of intelligence to embrace all human minds, all information in all languages, all the time. This approach – which treats the social world as an ecology – is the only one capable to dealing with the complexity present in a fluid international system typified by revolutions in the production and dissemination of knowledge, and in the character and dynamics of social relations as well as all attendant technologies.
The secret intelligence community (and the accompanying political apparatus) as one of the eight information-processing communities is – as a result of the failure to understand and adapt to these changes – so isolated that on its own terms it has become an irrelevance. More worryingly, it has become an expensive and unethical irrelevance that is undermining the craft of intelligence as a whole. I wish to restore the relevance of what I term the secret world—in the USA it now provides less than 4% of what national-level leaders need—but only in the context of a renaissance of intelligence that creates a Smart Nation and a World Brain focused on creating a prosperous world at peace by eradicating corruption, fraud, waste, and abuse. [2]
Intelligence should be an inherent responsibility of and benefit for all citizens, not just of leaders—80% of whom do not get intelligence support now.[3] We must migrate from secrets for the few to public intelligence for all.
Intelligence is Decision Support
What I present here represents the shift in my own scholarly focus from one that centred on a traditional perspective of nationally bounded intelligence activity to one in which the world’s population is taken as one informational ecology. Thus the craft of intelligence presented here is not for the benefit of one set of government actors, but is one that seeks to bring coherence within, between, and among the “eight communities” across all boundaries.
While it might be desirable to include several pages of definition here, I will simply point out a distinction between data (any raw single piece of information), information (integrated data with a narrative, generic in nature), and intelligence (both a process,[4] and a tailored answer to a given question – decision support). Intelligence is defined by the outputs, not the inputs.
In other words, data needs to be separated from noise and collated to create information, from which intelligence directly responsive to a need can be created. Information is the input, intelligence is the output.
The process of intelligence is a good one that should be understood, valued, and practiced by every citizen and demanded of every “leader.” Secret collection that is not processed is a symptom of failure, as is the neglect of open sources in 183 languages we do not speak (Olcott 2012). The cost to us—in tolerating local to global decision-making and investment that is at best incompetent and at worst a betrayal of the public trust—is now potentially catastrophic (Perrow 2009). What we do to ourselves every day out of ignorance is vastly more threatening than any possible combination of external predators.
Past critiques of the secret world that remain valid today are represented in one paragraph from a senior serving officer that bears on this chapter.[5]
The intelligence institutions have neglected support of judgment. This is partly due to being disinvited to help shape the sovereign’s judgment, but also partly due to mistaking who the sovereign has become. The people’s judgment is now being poisoned by ideologues who have filled the void. The situation is not honestly and soberly appreciated. Societal sense-making suffers due to the failure of the intelligence function and the craft to support it.
Three Eras of Intelligence
The craft of intelligence has gone through two eras and is now entering a third new era. The first era, running from the first days of recorded history and still to date, is the era of secret war, surreptitious entry and theft, and bribery to achieve ends inconsistent with those of the host country or target organization. In this tradition, intelligence is generally the province of governments, mixing dark side diplomacy and military spies, augmented by a separate track of agricultural and industrial espionage and bribery among multinational banks and corporations for whom practices that verge on the sharp and questionably ethical are a means toward illicit profit.[6] This remains—and wrongly so—the public perception of what “intelligence” is and should be.
The second era of intelligence, at least among the prominent Western nations and the USA in particular, was defined by Sherman Kent with his emphasis on strategic analytics (Kent 1965) but was immediately diminished by the unchecked expansion of clandestine and covert action operations, something never intended by President Harry Truman when he first authorized the Central Intelligence Agency (CIA) (Truman 1963).
The second era of intelligence also saw the emergence of very large commercial educational research programs as well as government and commercial research programs; and also Business Intelligence (data mining dashboards), Competitive Intelligence (narrow), and Commercial Intelligence (e.g. 360°). All of these failed to share data or evolve together. A modest literature on how the academy has failed to maintain its position as providing critical thinking skills to generations of students and in diminishing its place in providing original thought to the narrow and short-term ends of commercial and government contracts exists, as does a varied literature on bespoke research for the marketplace.
The second era also ushered in the use of technology, with collection displacing analysis while also failing to provide for processing of all that is collected. Coupled with the lack of outreach and the narrowness of external research efforts, the second era has failed to understand the world, including cause and effect. Ignorance has been the result.
The Third Era – Collective Intelligence
The third era is the era of the Smart Nation leading toward the World Brain and Global Game (the first is the content, the second the method), focusing on uniting the “eight communities” of intelligence, creating a Multinational, Multiagency, Multidisciplinary, Multidomain Information-Sharing and Sense-Making (M4IS2) network with call center nodes in each region, and ideally underpinning that with either an Open Source Agency under diplomatic auspices in the USA, or a privately-funded venture that upholds stated principles of integrity such as my mooted “Virgin Truth.”[7]
Collective Intelligence is in its infancy. The craft of intelligence must – will – eventually turn every citizen into a collector, producer, and consumer of intelligence (decision-support) in a pervasive manner not yet accepted by governments or corporations. Intelligence—decision-support—is an inherent responsibility of every citizen who wishes to foster democratic government, just society, and moral commerce.
The changing dynamics between the first two eras and the third are illustrated in Figure 1.
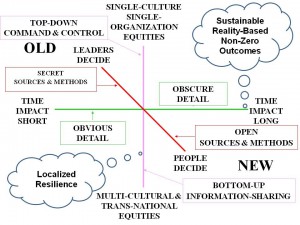
Figure 1: Context for Old versus Indigenous/New Intelligence
Corruption, market distortions and crime – especially financial crime – are “sand in the gears” of any economy or society. Intelligence — when properly led —is the lubricant of progress and of empowering the majority in society to drive individual and then economic growth. A reworked understanding of intelligence can use ‘truth’ as a lever and ‘trust’ as a source of intangible wealth.This is the diametric opposite of the prevailing culture of intelligence which supports the individual interests of nation states and businesses. But to bolster this aspirational larger end –of global open source intelligence – the secret intelligence capacity of all nations should be deployed as counterintelligence to protect the whole from internal corruption. With the one exception of counterintelligence, the third era is the era of “Open Everything,” emphasizing transparency and truth so as to provide decision-support to everyone from the citizen to the executive, building trust along the way. Vital to all of this is holistic analytics.
Figure 2 provides a visualization of where we have been and where we might go if we wish to respect reality – the top ten high-level threats to humanity – while also rapidly evolving our sources and methods to the fullest possible extent so as to serve all of humanity.
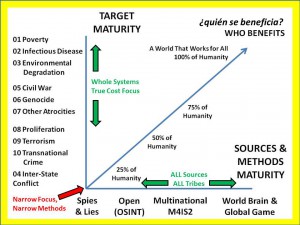
Figure 2: The Craft of Intelligence from Infancy to Maturity.
The ten high-level threats to humanity as depicted in Figure 2 are as identified and prioritized by LtGen Dr. Brent Scowcroft, USAF (Ret.), and other members of the United Nations High Level Panel on Threats, Challenge, and Change (United Nations 2004).
Poverty appears to do more damage to local, national, and global security in terms of survival and sustainability than all of the corporations put together—or the proliferating nations. The conventionally ignored five billion poor are also an infinite resource for changing how we do things, for creating infinite wealth with their most precious resource: their brains, knowledge and skill-sets (Prahalad, 2009).
Infectious Disease and Environmental Degradation (including Climate Change), threats two and three respectively, are absolutes. Today’s elite appear to have forgotten the lesson learned by the elite in New York City in the 1920’s, when public health for the poor was established precisely because infectious disease takes the rich as easily as it does the poor.
There are (at least) twelve core policy areas where the information must be shared and made sense of across all boundaries. They are listed below.
| 01 Agriculture02 Diplomacy03 Economy | 04 Education05 Energy06 Family | 07 Health08 Immigration09 Justice | 10 Security11 Society12 Water |
Figure 3: Twelve Policy Areas Demanding Transparent Sharing.
Combining these with the ten high-level threats results in a Strategic Analytic Model (EIN 2006) that frames the ten high-level threats across the vertical axis, and the twelve core policies across the horizontal axis, deepening the model by focusing particularly on the eight demographic challengers that are defining the future of Earth: Brazil, China, India, Indonesia, Iran, Russia, Venezuela, and Wild Cards such as the Congo, Nigeria, and Turkey.
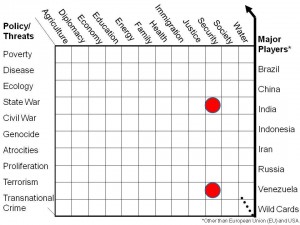
Figure 4: Strategic Analytic Model.
The two dots above, red when depicted in color, show where the secret world continues to focus: inter-state conflict and terrorism. All others (across the “eight communities”) tend to focus on one issue area in isolation or provide piecemeal linkages between issues. Except for myself, no one I know of is devising a comprehensive architecture for doing holistic reflexive analytics or focusing on doing the right thing instead of the wrong thing righter. (Ackoff 2004, Fuller 1969, Myers 2010).
This is a sense-making model for local to global multinational information-sharing and sense-making. This is a model that seeks to unify the “eight communities” and what should be, but is not, a robust national, regional, and global information commons. Only a global network—a near-real-time global network, will do. As David Weinberger puts it, in a room full of experts, the only true expert is the room itself. (Weinberger, 2012). It is the network—the World Brain and Global Game connecting all minds to all relevant information—the “whole”—that is smart, not the nodes.
In reflecting on “whither [conventional] intelligence,” it is helpful to contemplate the purpose of government and the role that intelligence could or should play in achieving that role. The Preamble of the US Constitution is a generic model.
We the People of the United States, in Order to form a more perfect Union, establish Justice, insure domestic Tranquility, provide for the common defence, promote the general Welfare, and secure the Blessings of Liberty to ourselves and our Posterity, do ordain and establish this Constitution for the United States of America.
Two of these four goals (establish justice, secure the blessing of liberty) should be considered to be counter-intelligence challenges. CORRUPTION in all its forms is a major target for the new global form of intelligence outlined here. The other two (domestic tranquility, promote the general welfare) are intelligence/decision-support challenges that are best served by open sources and methods. In all four areas, domestic enemies are central actors (Taibbi 2012, North 2012).
Most governments, less Iceland specifically and the Nordics generally, are not actually working in the best interests of the 99 per cent – their larger publics. Western governments have been captured by banks and corporations (Taibbi 2010).
Information Costs Money, Intelligence Makes Money
I first recognized the market distortions inherent in the information industry in the 1990’s, when I understood that the emphasis was misplaced – on selling and buying massive amounts of information without being able to make sense of it, never offering a precise answer for a precise price.
At the same time, I began to recognize the fragmentation of knowledge and the fragmentation of the marketplace of knowledge. Below is my first attempt to get a grip on the generic structure of knowledge that must be integrated.
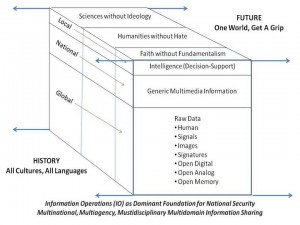
Figure 5: Information Cube.
On the next page is another depiction of the information topography; various communities continue to resist maturation toward holistic information ingestion and exploitation culminating in organizational intelligence.
Most of the world, including most of the major governments and corporations, are in Quadrant I, leveraging current internal knowledge (but forgetting much of what they know from year to year). A major impediment to maturing on the information side is the continued retardation of the inherently closed, selfish, and often dangerously insecure and misleading information technology (IT) marketplace still rooted in fragmentary proprietary “solutions.”
Emerging information networks including many civil advocacy groups are in Quadrant II, utilizing the Internet as a host and social productivity as a mind-set for sharing information, but with a very troubling lack of structure, historical and cross-disciplinary coherence, or the ability to produce actionable intelligence that can mobilize voices outside of one isolated issue at a time. None seem to understand that it is not social media that matters, but rather the social operating system that uses social media (Rheingold 2012).
Few are able to master Quadrant III, not for lack of access or money, but for lack of mind-set and appreciation for the new craft of intelligence. Most of the deep knowledge needed has not been published. Indeed, the acme of skill for the modern analyst is to know who knows, to bring the consumer and the individual external producer together so as to shepherd the creation of new tailored intelligence precisely suited to the need in real-time. This is not something that can be done by young people oppressed by 1950’s security mind-sets, deprived of access to 21st Century technology, and limited in their ability to find, much less exploit, humans who do not have the citizenship, clearances, or other burdensome access “qualifications” imposed on analysts by security mandarins.
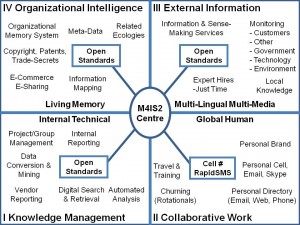
Figure 6: Four Quadrants of Information to Intelligence.
Then we have Quadrant IV, visualized and documented in the 1960’s (Wilensky 1967), and never heard from again. Today’s governments and corporations continue to suffer from lost knowledge due to high turnover and inadequate tools and practices for retaining all knowledge once acquired.
Time & Transparency
When taking the long view, it is most difficult to justify secrecy. (Herman 1996). At the same time transparency has a value so great that any effort to impose secrecy beyond a short tactical timeframe is deleterious to the broader interests of the society affected (Brin 1999).
Despite the fact that open intelligence appears more urgently needed for all elements of government and society, than secret intelligence against a non-existent conventional power threats or dubious terrorism threats, all “eight communities” persist in embracing secrecy (or proprietary) and hoarding over transparency and sharing, serving the few over the many. The inherent good in open society has been subverted by closed corruption.
The (new) craft of intelligence, in my view, must seamlessly integrate education, intelligence, and research, on a foundation of “open everything.”
Geospatial Dimension
In 1988 I pointed out to the General Defense Intelligence Program (GDIP) annual meeting that geospatial attributes were essential if we were to get to machine-speed all-source fusion. Still today the secret world refuses to be serious about this fundamental pre-requisite and foundation for being able to do machine-speed all-source fusion.
There is however very good news, and here I single out Dr. Patrick Meier, whose blog iRevolution provides regular updates about the intersection of geospatial information, open source software, and crowd-sourcing: where diasporas not only plot events and observations on a digital map, but also translate Short Message Service (SMS) texts from 183 languages into English.
Human Dimension
Human intelligence is central to the craft of intelligence—technology is not a substitute for thinking—to which I would add James Bamford’s point that no one has yet built a computer equal to the human brain (Bamford 2001). My monograph on Human Intelligence: All Humans, All Minds, All the Time is easily found online, as is the graphic with Jim Bamford’s full quote.[8]
Information Pathologies
Across current knowledge production industries there are a disturbing number of persistent information pathologies that enable those who wish to prey on the uninformed to do so at will. Such pathologies include: a culture of cheating, propaganda and PR, forbidden knowledge, missing history, manufactured consent, false science, secrecy, false instruction, and outright lies. The secret world distinguishes between “denied areas” and “hard targets” at the same time that it rejects doing what it calls “global coverage.” (Sutton 2006). What no one in the secret world appears willing to acknowledge is that without global coverage, and without a full and complete understanding of what is available from legal and ethical open sources of information (including direct local knowledge not published), it is, as one author has put it, “spying blind” (Zegart 2009). Everyone else neglects history, to their detriment (Gaddis 2004), as well as foreign language and foreign cultural studies including foreign literature (Hill 2011, Olcott 2012).
The craft of intelligence as practiced today also refuses to acknowledge the importance of steady-state and “true cost” economics (Daly 1991, 1993, 1994, 2010), called by some the triple-bottom line (ecological and social as well as financial costs). As the world begins to recognize that beyond peak oil we face peak water; that chlorine and other toxins are externalized costs that cause current illness while imposing future social and ecological costs on future generations, one has to ask:
What is the point of a “secret” intelligence community that produces so very little for the top leaders and nothing for everyone else?
A single cotton undershirt “costs” 570 gallons of water, 45 per cent of that in irrigation; 11-29 gallons of fuel; child labor at 50 cents a day across any of 17 countries; and it emits a number of volatile compounds including Nox, SO2, CO, CO2, and N2O (Liszkiewicz 2010). Within a single country, the USA, there is no “national” grasp of our vulnerability to breaking levees across nearly every county in the land, many built to the lowest engineering and financial standards possible (Boyd 2009); there is no “national” grasp of the nation-wide vulnerability to industrial-based biological, chemical, and radiological catastrophes all too possible (Perrow 2011, Denninger 2011).
Meanwhile, false US Government statistics misrepresent the unemployment rate (it is 22.4 per cent, not 8 or 9 per cent) and falsely claim new jobs rather than job losses (Roberts 2012). Other countries appear to have similar issues.
How is one to cope with a government that does not tell the truth, corporations that do not tell the truth, media that do not tell the truth, even schools that do not teach the truth nor how to grasp the truth?
This is the challenge of our times, and this is the challenge toward which I seek to direct the craft of intelligence in the 21st Century.
What Is To Be Done?
With the exception of robust counterintelligence against domestic threats, I champion “Open Source Everything.” The figure below illustrates both our challenge and our objective.
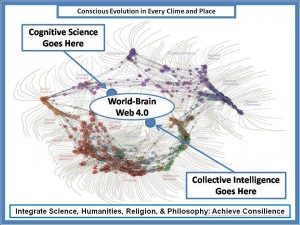
Figure 7: Toward the Unity of Knowledge.
Figure 7 depicts the fragmentation of academic disciplines and sub-disciplines. [9] Similar divisions also characterize the other seven communities of information and intelligence. The developed world has achieved a modern variant of the proverbial Tower of Babel, creating a system that seems incapable of holistic coherent sustainable analytics!
If we cannot create a craft of public intelligence that achieves both inter-community and multi-national information-sharing and sense-making, then the ethical and environmental challenges we face as a species may well overwhelm us.. There must be a “priority of effort” toward first creating an ’autonomous Internet’ (one that cannot be shut down by any government or corporation) that delivers the “six bubbles” shown below to the affluent one billion; and then is rapidly expanded toward embracing and empowering the five billion poor with free cell phones and cell phone service for at least three years, along with access to multi-lingual call centers that educate each poor person—many illiterate but not stupid – “one cell call at a time.”[10]
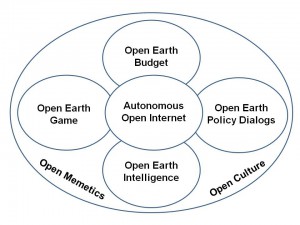
Figure 8: Autonomous Internet for a World Brain and Global Game.
Below is my comprehensive architecture for connecting all humans to all information in a manner that produces pervasive intelligence for all.
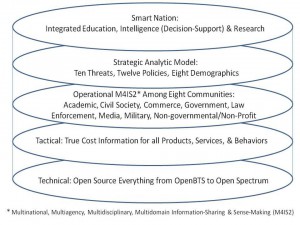
Figure 9: Comprehensive Architecture for Global Intelligence
It is not possible here to address the emerging disciplines of cognitive science and collective intelligence; both are severely constrained by the generally isolated and insular nature of each of the “eight communities”, but some intellectual progress is being made (Atlee 2002, 2009, 2012; Tovey 2008).
The two preceding objectives cannot be accomplished without a radical change in how we conceptualize and implement security within networks.[11] To be scalable at an affordable price, and to avoid the pathologies associated with proprietary software and hardware, the craft of intelligence must demand and embrace an “open source everything” approach as illustrated below. Robert Garigue’s lasting contribution to this field is this: security is about creating and maintaining trust among individuals. [12]
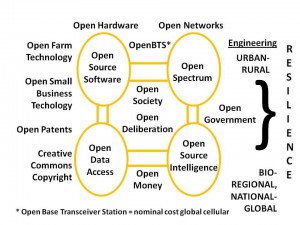
Figure 10: Open Source Everything and the Autonomous Internet.
We all need to discuss the open source everything approach and the transparency, truth, and trust that it seeks to foster world-wide, at every level from neighborhood to regional water authorities and more, elsewhere — this is particularly so with respect to shared information and the shared burden of sense-making from local to global (Olcott 2012). No other approach is affordable and therefore scalable. No other approach yields a good outcome.
There is so much more to be integrated into the craft of intelligence as we go forward together, but it is important to bring this chapter to a close and do so with one word and one final graphic.
The word is INTEGRITY. We have lost our integrity across all “eight communities”, and become cheating cultures with little accountability within governments, banks, corporations, even universities, trade unions, and religions. If we can share one word as an operational principle going forward, that word is INTEGRITY.
A reworked understanding of intelligence that is based on open everything, an open source principle that is premised on transparency, integrity and a global commons. There are clearly considerable barriers to entry for this revised system of intelligence: vested commercial and intelligence interests have profited from the closed and fragmented system that is currently in place. It would also seem unlikely – therefore- that they would be prepared to step aside for an open source system readily. However, it seems clear to me that the open-source everything transformation could begin as a start-up with funding via philanthropic sources, and then take on crowd-sourced funding as its value is demonstrated. The open source revolution described here is potentially very profitable, in keeping with the concepts developed by C.K. Prahalad with respect to “the fortune at the bottom of the pyramid” (Prahalad 2009). And thus the principle of open source intelligence could be used as an alternative and empowering form of economic development in the developing world, and within developed societies too. Such a system would also radically reorient the international system away from a narrow and aggressive competition between self-seeking states and corporations and towards greater cooperation.
I wish to conclude, most humbly, with an illustration of a strategy for creating a prosperous world at peace, a strategy that requires only that the public pay attention and demand “open everything.”
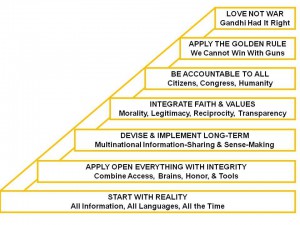
Figure 11: Strategy for Creating a Prosperous World at Peace.
Bibliography
Ackoff, Russell (2004) “Transforming the Systems Movement” PLA Conference Paper, 26 May HTTP: <http://tinyurl.com/Ackoff-Prime>.
Atlee, T. (2012) Empowering Public Wisdom: A Practical Vision of Citizen-Led Politics, San Francisco, CA: Evolver Editions.
_____ (2009) Reflections on Evolutionary Activism, Seattle, WA: CreateSpace.
_____ (2002) The Tao of Democracy: Using co-intelligence to create a world that works for all, Seattle, WA: BookSurge
Bamford, James (2001) Body of Secrets: Anatomy of the Ultra-Secret National Security Agency, New York, NY: Doubleday.
Bean, Hamilton (2011) No More Secrets: Open Source Information and the Reshaping of U.S. Intelligence, Santa Barbara, CA: Praeger.
Boyd, Ezra (2009) “Large Map of US counties with levees,” Levves.org, New Orleans, HTTP: <http://levees.org/large-map-of-u-s-counties-with-levees/>
Bozeman, A.B. (1998) Strategic Intelligence and Statecraft: Selected Essays, Dulles, VA: Brassey’s Inc.
Brin, David (1999) The Transparent Society: Will Technology Force Us To Choose Between Privacy And Freedom? New York, NY: Basic Books.
Daly, Herman (2010) Ecological Economics: Principles and Applications, 2nd edn. Washington, DC: Island Press,
_____ (1994) For the Common Good: Redirecting the Economy toward Community, the Environment, and a Sustainable Future, Boston, MA: Beacon Press,
_____ (1993) Valuing the Earth: Economics, Ecology, Ethics, Cambridge, MA: The MIT Press, Cambridge.
_____ (1991). Steady-State Economics: With New Essays, 2nd edition, Washington, DC: Island Press,
Davis, Jack (1986) “Competing Influences on the Policymaker,” as 2000, pp. 46-53.
Denninger, Karl (2011) Leverage: How Cheap Money Will Destroy the World, Hoboken, NJ: Wiley.
Durant, Will (1916) Philosophy and the Social Problem: Annotated Edition (2008), Frisco, TX: Promethean Press.
Earth Intelligence Network (2006) “Reference: Earth Intelligence Network Analytic Concept”, HTTP: <http://tinyurl.com/EIN-2006>.
Esiemokhai, E.O. (2012) “National Security, Military Intelligence, and You,” Nigerian-Newspaper.com, 31 July 2011. HTTP: <http://nigerian-newspaper.com/national-security.htm>.
Fuller, R.B. (1969) Ideas and Integrities: A Spontaneous Autobiographical Disclosure, New York, NY: Macmillan.
Gaddis, J.L. (2004) The Landscape of History: How Historians Map the Past, Oxford, UK: Oxford University Press.
Garland, Eric (2012), “Peak Intel: How So-Called Strategic Intelligence Actually Makes Us Dumber, The Atlantic (online), 5 April 2012. HTTP: http://tinyurl.com/Garland-Intel
Herman, Michael (1996) Intelligence Power in Peace and War. Cambridge, UK: Cambridge University Press.
Hill, C. (2011) Grand Strategies, Literature, Statecraft, and World Order, New Haven, CT: Yale University Press.
Kahn, D. “An Historical Theory of Intelligence.” Intelligence and National Security 16, no. 3 (Autumn 2001): 79-92.
Kent, S. (1965) Strategic Intelligence for American World Policy, North Haven, CT: Archon Books.
Liszkiewicz, J.Z. (2010), “True Cost of One White Cotton T-Shirt,” Reconfigure, HTTP: <http://true-cost.re-configure.org/true_cost_shirt.htm>
Marchetti, V and J.D. Marks (1976) The CIA and The Cult of Intelligence, Philadelphia, PA: Coronet Books,
Mitelman, L.T. (1974), “Preface to a Theory of Intelligence.” Studies in Intelligence vo1. 8, no. 3 (Fall 1974): 19-22.
Myers, K.C. (2010) Reflexive Practice: Professional Thinking for a Turbulent World, New York, NY: Palgrave Macmillan.
North, Gary (2012) “Administrative Law (New World Order) versus Democracy (Live free or Die),” Phi Beta Iota Public Intelligence Blog, 4 February 2012, HTTP: <http://tinyurl.com/North-Admin-Law>.
Olcott, Anthony (2012) Open Source Intelligence in a Networked World. New York, NY: Continuum International Publishing.
Perrow, Charles (2011) The Next Catastrophe: Reducing Our Vulnerabilities to Natural, Industrial, and Terrorist Disasters, Princeton, NJ: Princeton University Press.
Pillar, Paul (2011) Intelligence and U.S. Foreign Policy: Iraq, 9/11, and Misguided Reform, New York, NY: Columbia University Press.
Prahalad, C.K. (2009) The Fortune at the Bottom of the Pyramid: Eradicating Poverty Through Profits, Saddle River, NJ: Pearson Prentice Hall.
Rheingold, H. (2012) NET SMART: How to Thrive Online, Cambridge, MA: MIT Press.
Rischard, J.F. (2003) HIGH NOON: 20 Global Problems, 20 Years to Solve Them, New York, NY: Basic Books.
Roberts, P.C. (2012), “December Net Jobs a 12,000 LOSS – Actual Unemployment 2.6 Times Official Rate or 22.4%,” Phi Beta Iota Public Intelligence Blog, HTTP: <http://tinyurl.com/Roberts-22-4>.
Steele, R.D. (1988-2012) All articles & chapters, briefings & lectures, books, videos, etcetera, easily accessed online. HTTP: <http://tinyurl.com/Steele2012>.
Sutton, Boyd (2006) “Global Coverage, Looking Backward, Looking Forward,” Phi Beta Iota Public Intelligence Blog 24 December 2006, HTTP: <http://tinyurl.com/Sutton-2006>.
Taibbi, M. (2010) Griftopia: Bubble Machines, Vampire Squids, and the Long Con That Is Breaking America, Spiegel & Grau.
Taplin, W.L. (1989), “Six General Principles of Intelligence.” International Journal of Intelligence and Counterintelligence 3, no. 4 (Winter 1989): 475-491.
Tovey, M. (2008), COLLECTIVE INTELLIGENCE: Creating a Prosperous World at Peace, Oakton, VA: Earth Intelligence Network.
Treverton, Gregory (1986) “Producer versus Consumer Outlooks,” Steele 2000, pp. 48-49, cf. Figures 11-12.
Truman, H. (1963) “Limit CIA Role to Intelligence,” The Washington Post, 22 December 1963, A11. HTTP: <http://tinyurl.com/Truman-CIA-63>.
United Nations (2004), A More Secure World: Our Shared Responsibility, High-Level Panel on Threats, Challenge, and Change, New York, NY: United Nations.
Weinberger, David (2012). Too Big to Know: Rethinking Knowledge Now That the Facts Aren't the Facts, Experts Are Everywhere, and the Smartest Person in the Room Is the Room, New York, NY: Basic Books
Wilensky, H.L. (1967). Organizational Intelligence: Knowledge and Policy in Government and Industry, New York, NY: Basic Books.
Wilson, E. O. (1999). Consilience: The Unity of Knowledge, New York, NY: Vintage.
Wright, Robert (2001). Nonzero: The Logic of Human Destiny. New York, NY: Vintage.
Zegart, A.B. (2009). Spying Blind: The CIA, the FBI, and the Origins of 9/11, Princeton, NJ: Princeton University Press.
About the Author
Robert David STEELE Vivas, (60), is CEO (pro bono) of Earth Intelligence Network, a 501c3. He served for nine years as a spy with additional responsibilities in advanced analytics, counterintelligence, information technology, and overhead system program management. An honorary hacker since 1994, he was among the first to call for cyber-security standards and education, and also the first to conceptualize a “Smart Nation” in which education, intelligence, and research are seamlessly integrated. He served in addition four years active duty as a Marine Corps infantry officer and S-1/Adjutant, sixteen years as a Reserve intelligence officer, and five years as the second ranking civilian for Marine Corps Intelligence, where he was the senior civilian responsible for creating the Marine Corps Intelligence Center in 1988, and the Study Director for the first global intelligence study to create strategic acquisition generalizations, Planning and Programming Factors for Expeditionary Operations in the Third World (MCCDC, 1990). Author of many books, articles, and chapters, he is also the #1 Amazon reviewer for non-fiction, reading and reviewing in 98 categories accessible at Phi Beta Iota the Public Intelligence Blog.
Endnotes
[1] See also Wilson 1999, Weinberger 2012.
[2] General Tony Zinni is cited with respect to 4%, in my chapter on “Open Source Intelligence” Loch Johnson (ed.) Strategic Intelligence (Volume 2 Chapter 6), Santa Barbara, CA: Praeger, pp. 95-122
[3] The secret world is focused on “hard targets” (a very few) instead of “global coverage” (everything always), and also focused on impressing the top political leader(s) rather than providing balanced support to all elements of the government or to society at larger. Cf. “Intelligence for the President—and Everyone Else,” Counterpunch, Weekend Edition Feb 29-Mar 02, 2009.
[4] Requirements definition, collection management, source discovery and validation, multi-source fusion with machine and human processing, machine and human analytics, and timely actionable presentation to a decision-maker in a form that is useful and portable.
[5] Anonymous. A still valid statement from the 1990’s, by Ellen Seidman, then Special Assistant to the President on the National Economic Council (Steele 2008a: 124):
CIA reports only focus on foreign economic conditions. They don't do domestic economic conditions and so I cannot get a strategic analysis that compares and contrasts strengths and weaknesses of the industries I am responsible for. On the other hand, Treasury, Commerce, and the Fed are terrible at the business of intelligence — they don't know how to produce intelligence.
Ralph Peters has described to me the challenge of 10,000 elephants each being examined by a 100,000 blind men, none of whom talk to each other.
[6] See HTTP:<http://tinyurl.com/Steele-Craft-Refs>. Relevant here are Esiemokhai 2011, Kahn 2001, Marchetti & Marks 1976, Mitelman 1974,Taplin 1989.
[7] “Open Source Agency Executive Access Point,” online at HTTP: <http://tinyurl.com/OSA2011>. My one-pager to Sir Richard Branson never reached him. It can be viewed online at HTTP: <http://tinyurl.com/Steele4Branson>.
[8] HTTP: <http://tinyurl.com/NSA-BRAIN>
[9] The foundation image above came from Dick Klavans, long a pioneer of citation analytics, and more recently a founder of Maps of Science. Cf. Maps of Science, HTTP: <http:mapsofscience.com>. See also Wilson 1999.
[10] Earth Intelligence Network 2006.
[11] For a more nuanced discussion of old versus new cyber-security mindsets, see <Who’s Who in Cyber-Intelligence: Robert Garigue>.
[12] Ibid.
Short URL to This Post: http://tinyurl.com/IntelCraft21
Citation: Robert David Steele, “The Evolving Craft of Intelligence,” in Robert Dover, Michael Goodman, and Claudia Hillebrand (eds.). Routledge Companion to Intelligence Studies (Oxford, UK: Routledge, 31 July 2013)



