U.S. Struggles with ‘Electronic Fratricide’ in Afghanistan
November 17, 2009, Nathan Hodge
In Afghanistan, western militaries use radio frequency jammers to keep troops safe from remotely-detonated bombs. But those jammers and other gadgets have contributed to a “pollution” of the airwaves so severe that over 200 systems at Afghanistan’s main air base can’t talk to one another.

Senate Panel: 80 Percent of Cyber Attacks Preventable
November 17, 2009, Kim Zetter
If network administrators simply instituted proper configuration policies and conducted good network monitoring, about 80 percent of commonly known cyber attacks could be prevented, a Senate committee heard Tuesday.
Phi Beta Iota: Below the fold see the technical threat slide from Dr. Mich Kabay, and accompanying words, as presented to NSA at the first public conference in Las Vegas in January 2002. We have learned NOTHING since then, and the Office of Management and Budget (OMB) is as catatonic as any so-called “Presidential” oversight agency could be…..our ignorance in the cyber-arena is halfway toward matching our ignorance in the intelligence arena–$75 billion a year for 4% of what the President needs, while we ignore 95% of the open sources in 183 languages we do not speak. At a more strategic level, we could buy peace three times for what we spend on war.
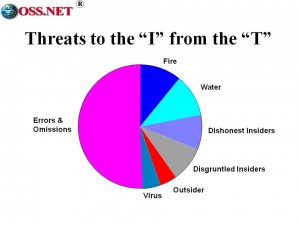
As I begin my technical conclusion, I want to start with some rough estimates about sources of loss within computer systems & data.
Badly devised “T” is a much greater threat to the “I” than deliberate attack.
We lose half the value of our data to errors and omissions caused by mediocre data ingestion programs.
You’re off the hook on the 20% lost to fire and water–that’s simply bad management, with either no data back-up or data back-up files stored in the same room as the core data files.
Dishonest and disgruntled insiders do the most deliberate damage, in part because our systems are generally not designed to detect authorized users doing unauthorized things.
Only at the very end do we see viruses, many of which arrive in shrink-wrapped factory software and hardware, and outsider attacks.
The bulk of our technical threat is one of our own making.
Mich E. Kabay, The NCSA Guide to Enterprise Security: Protecting Information Assets (McGraw-Hill, 1996) ISBN 0-07-033147-2. Chapter 1, Figure 1, page 11. The figure in the book is superseded by this table, provided by Dr. Kabay in personal communications to Robert Steele, OSS CEO, 12 March 1998.