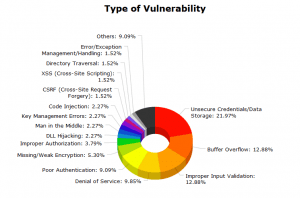
Cyber-Integrity – Is Bad Code the Horseshoe Nail that Costs Us Everything?
Cyber-Integrity – Is Bad Code the Horseshoe Nail that Costs Us Everything?
CIA created the Artificial Intelligence Staff (OIT/AIS) around me in 1986. I quickly learned that all code lacked documentation and was full of holes. By 1994 I was the invited opening speaker for Hackers on Planet Earth, invited to join the Silicon Valley Hackers / THINK conference of which Larry Page is among the more notorious members, and I wrote the below warning letter to the White House that was ignored.
1994 Sounding the Alarm on Cyber-Security
None of these issues are new. Banks have been suffering from hacks costing trillions but have kept it quiet because banks lack the integrity to clean their own house and the last thing they want is a system that would interfere with the movement of dirty money. I find it amusing that the Microsoft president would call SolarWinds hack an “act of recklessness. He is not stupid – just corrupt to the bone. He knows that Microsoft – and Microsoft updates – are the primary means of infecting or gaining access to almost every laptop and desktop target world-wide.
- US: Hack on Government Agencies Goes Beyond SolarWinds Users
- Microsoft president calls SolarWinds hack an “act of recklessness“ – Of 18,000 backdoored servers, hackers followed up on only a few dozen.
- Who Has Been Affected by the Huge SolarWinds Cyberattack so Far?
- Microsoft Breached Via SolarWinds As Scope Of Destruction Widens: Report
Suspected Russian hackers capitalized on Microsoft’s wide use of SolarWinds to infiltrate the software giant, and then used Microsoft’s own products to further their attacks on other victims, Reuters said. Microsoft pushed back on the report.
- Pentagon Forces Emergency Shutdown of Computer Network Handling Classified Material
- Data crunching consequences of SolarWinds cyberattack
- Hackers used SolarWinds' dominance against it in sprawling spy campaign
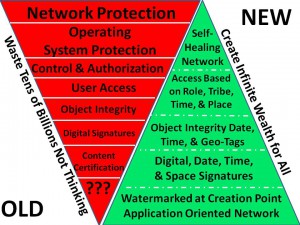
In 1997 I created the below graphic under the intellectual and experiential leadership of Robert Garigue (RIP) and communicated it to the US Government via various channels. Again, ignored.
Here are three emails I received from very well-placed sources on the current situation:
Subject Matter Expert #1:
There may have been a back door by somebody on the inside paid off or there was a legitimate bug which got taken advantage of.
My contact said he know they penetrated what programmers call the GOD layer of Code. This means the hacker embedded within the code with several lines of code a way to have a back door. The back door then phones come to a website set up the hackers to first a trusted website then anywhere it wants to go. When the software was send out as an update then the hackers could get into any company which has uploaded the code. Apparently where are 1800 organizations with the update. It does not mean all 1800 where penetrated but it means the hackers got signals back from many sites that uploaded.
It will be many months before the full impact is known as the starting point in the solar wind computers followed by the all the computers which hacked the software. The fear is that the software upload may have updated with multiple back doors and written itself multiple more on the inside. There are ways to hide things on the inside of all these organization such that they are leaky for years to come.
The contact told me to get out of software stocks in general for a while. Chip stocks will be safe but this is an event which could cause a rippling melt down.
The list of the 1800 organization is unknown but many organization of national security have been compromised.
My contact says Solar wind bought a Calgary startup company about one year ago called Passportal. He worked there and wrote big chunks of the security software.
Passportal was bought because they had a good corporate security system and solar wind intended to incorporate it into their own software. It never happened but they were in progress but it was with a few months of release.
He knows lots of solar wind folks both sides of border. The ship is starting to leak as folk jump overboard. Software guys knows that damage done to the US government with the botched update will means that the company will collapse as nobody will use their software again.
Subject Matter Expert #2:
Bad news. No specific fix because info is fragmented and those affected cannot talk because of legal liability. Cool tactic by an adversary.
Yep, resellers and integrators of SolarWinds should be about 9.99 on the pucker scale about now. Many of these cyber security firms' managers believe what the art history majors who work in their firms' marketing departments write down. Serves them right, but the bad actors who did this are sending a big time message: “We have access.”
End quotes.
I personally doubt this is the Russians. The Chinese – working for the Rothschilds – are far more likely, and I want to stress that I believe the Israelis and the government of the United Kingdom are also engaged.
We are in a fight to the death between good and evil. This attack, like the fake pandemic, is a variation of the Zionist threat to the USA and other Western countries, known as the Sampson Option. The cover-up story is that Israel simply wanted nuclear weapons to protect itself from the Arabs. The actual story is that Israel has been using nuclear weapons planted in major Western cities – along with bribes and pedophilia blackmail a la Epstein – to get countries to screw their public in favor of whatever Israel – never to be confused with Judaism – wanted.
Since the 1980’s when the Zionists discovered the ease with which software systems could be penetrated – the book review below is a small window into that – Sampson Option 2.0 has been the threat of a catastrophic attack on software systems that would take down banking, electricity, and energy and water pipelines as well as communications and computing across governments and the private sector.
Review: Robert Maxwell, Israel’s Superspy–The Life and Murder of a Media Mogul
Just as the US Government ignored my warning in 1994, so also have all institutions refused to be serious about keeping their SCADA or Supervisory Control and Data Acquisition systems, isolated from the Internet (and from powerlines, the Chinese have been riding our power lines into computers not connected to the Internet for over 20 years – think Best Buy Ethernet extender that you plug in on one floor from the router, and then plug out on a second floor. Hackers (not to be confused with criminals) have been sounding the alarm on this since the early 1990’s with Winn Schwartau in the lead, as well as officer students at the Air War College.
Source: http://www.securenetconsulting.co.uk/p/scada.html
There are a tiny handful of people qualified to help fix this. I know half of them. If the President were to direct the creation of the Open Source Agency (OSA), twice approved by OMB at FOC $2B, I could create Web 3.0 as an adjunct to the quantum financial and voting systems, and get us back on track. My initial council of six – there are another six to be recruited but we know who they are to be – has agreed that we need to walk away from the termite infested collective known as the “IT Industry.” There are many individual talents who can be harnessed in support of a new Manhattan Project / Marshall Plan / Moon Shot but the companies themselves are 80% dead meat – managers without integrity.
Here are a few links today from one of America’s greatest IT truthers, now retired, but available to the President (or the Pentagon) as a true patriot interested in making things right.
- Zipper the SIPR: The SolarWinds Blow
- Explaining the 2020 End of Year Cyber Hack of Big, Fat Targets of Opportunity
- Fixing the American Internet: Got the Plague? Burn Aromatic Herbs. Works Great, Right?
- Google: High School Science Club Mini Revolt. Mini? Why Not Maxi?
Stephen E. Arnold is the man who wrote The Google Trilogy in the 1990’s and was ignored. Today he is writing Arnold’s Laws of Online Information.
I asked Brother Stephen, one of my most respected colleagues, if he had a one-page POTUS brief I could hand off toward the President. Here is his answer:
I do not need a page. Investigate. Right now there is a “fact void.”
As we have seen with election fraud, despite heroic efforts by Mike Flynn, Sidney Powell, Lin Wood, Peter Navarro, and others including Rudy Giuliani – and as we saw with the Russian witchhunt – those who are normally charged with investigating, including the FBI, the CIA, and the Cabinet Agencies, do not want to investigate because they are wholly-owned subsidiaries of the Deep State and they know that investigation will lead to indictments, convictions, incarcerations, and in some cases, execution.
For myself, this is a simple matter. Either we are to have integrity in government and integrity in the data and data system that underlay government and banking and everything else, or not. My vision for an OSA that could give the President a rapid triage on this problem, including a Center for Computational Integrity such as I proposed in 1994, is below.
Smart Nation Vision – By Invitation
Related and integral to the above are my long-standing ideas on the need for an Autonomous Internet that offers the four Individual Sovereignty enablers defined so ably by Kaliya “Identity Woman” Young: Anonymnity, Identity, Privacy, & Security. In 1986 within CIA I spoke to the need for data at rest encryption. No one wanted to hear it. CIA and the rest of the secret world that works for the Deep State wants total transparency – and a total lack of sense-making tools – across the 99% information ecology, and they don’t much care if their secret shit is compromised because it is just not worth what we are paying for it.
Here is just one graphic from my Autonomous Internet pile.
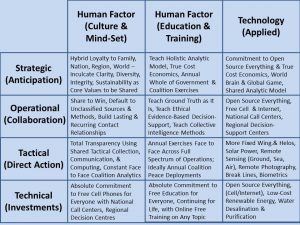
There is no one – NO ONE – in the US Government capable of thinking like this, much less acting on these ideas. WE NEED AN OPEN SOURCE AGENCY REPORTING TO THE PRESIDENT.

NOTE: After writing this for The Steele Report, I decided this topic is of such high public interest that I feel obligated to post it publicly. See the Table of Contents for past and forthcoming Reports here. For $11 a month or $99 a year I deliver a text report with links and graphics each Monday and an interactive video webinar where I answer questions each Saturday.