
Interesting concept, although I'm not sure how practical it is.
Towards a Cyber Leader Course Modeled on Army Ranger School
By Gregory Conti, Michael Weigand, Ed Skoudis, David Raymond, Thomas Cook and Todd Arnold
Small Wars Journal | Apr 18 2014 – 11:31am
Since 1950, the U.S. Army Ranger School has garnered a well-earned reputation as one of the most demanding military schools in the world. Graduates have served with distinction in special operations units including the Ranger Regiment and Special Operations Command as well as line units throughout the Army. With the emergence of cyberspace as an operational domain and the critical shortage of technically and operationally competent cyber[i] leaders, the time has come to create a U.S. Army Cyber Leader Course of equal intensity, reputation, and similar duration,[ii] but focused on cyber operations (see Figure 1). This article presents a model for the creation of such a school, one that goes far beyond just a tough classroom experience by using tactical close-access missions as a core component. What we propose is unique, demanding, immersive, and fills a necessary gap in Army cyber leader development. This article is a condensed form of a more detailed analysis and description of the proposed Army Cyber Leader Course.
PDF (14 Pages): Army Cyber Leader Course Concept SWJ
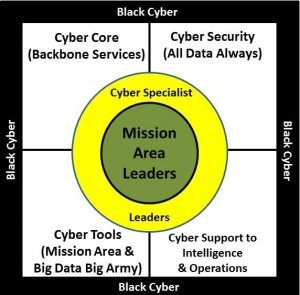
Phi Beta Iota: Army commanders are on record as saying that Information Operations (IO), which is not to be confused with Cyber or Intelligence, it encompasses both, take up to 80% of their time but only receive 1% of the budget. This is analogous to the infantry, which is 4% of the force, takes 80% of the casualties, and receives 1% of the budget. The paper is an excellent foundation for going much further. Education and training must distinguish among end-user mission area leaders and specialist cyber leaders; white cyber versus black cyber, cyber core versus cyber tools, and cyber counterintelligence versus cyber intelligence. Cyber must embrace the four C's: Connectivity, Content, Coordination of R&D and Investment; and C4 Security. This graphic illustrates our perspective on this vital topic. As now defined, the concept applies to specialists in cyber as traditionally managed by the G-6 and the SIGINT element only of the G-2. If extended, it should apply to cyber as conceptualized, developed, and fielded across every mission area in the attack and in the defense. It would also be helpful to offer cyber leadership craftred for each of the four levels — strategic, operational, tactical, and technical. Big Army has destroyed cyber and logistics with contractors — we are long overdue for reversing the insanity of not being able to go to war without one contractor per laptop. Hence, the most important cyber decision of all may be the decision about who will “do” cyber in every clime and place.
PPT: Army Cyber Concept Expansion
See Especially:
1995 Creating a Smart Nation: Strategy, Policy, Intelligence, & Information
1995 National Information Strategy 101 Presentation to CENDI/COSPO
See Also:
Information Operations @ Phi Beta Iota
Selected Comment from Small Wars Journal:




As a former member of the AF Cyberwarfare and A6 communities for the past decade and John Boyd acolyte from 1982, I cannot disagree more with the authors. I'm one of the old guys with a real engineering degree who was one of the creators of the entire Network Security Barrier Reef Program in the last half the 1990's.
Our problem is a lack of leadership. I'm not writing about a man or woman with rank but real leadership, not a claim of leadership that they think their rank has granted them. In addition and worse is a lack of Knowledge, Skill and Ability (KSA's) in the career field, lack of understanding business and operational cases for making a good decision. Then there is the careerism problem. Power Point Ranger briefings for the sake of useless no value added briefings and the endless bucking of decisions up the chain.
A few years back the AF Cyberwarfare command decided that all A6 Cyberwarfare senior enlisted, officers and Fed Civilians MUST take and pass with a 90% or higher a SIPRnet training course Introduction to Cyberspace Warfare. It had been created by a few National Guardsmen who on paper looked like experts but the training was full of factual technical mistakes. Naturally management demanded that all take it in five days and put all real work on-hold. The Brass used the passing scores for the military sods as a retention vice no-retention cut threshold.
The AF Cyberwarfare command didn't want to know if the training was valid, accurate or truthful. No feedback wanted. Just do it and move on. Me, I quit writing down factual inaccuracies in the course when I hit forty pages because the recently promoted yes-boy of the day was more concerned that I wouldn't complete the training in the time he allotted. Because of the inherent infrastructure problems with SIPRnet the training required about 56 hours to complete instead of the 34 hours the training syllabus stated. For us civilians, no overtime was authorized so this went over like cement shoes on the plank deck of a boat.
Ignorance is bliss and low ethics in todays DoD just so long as you are Politically Correct brown noser.
Since 2006 I noticed countless officers taking useless training courses just so the long list of training courses completed would look good to the promotion board. Then there was the training courses that were used to cut people, not really educate them.
Then we have the entire Officer corps that knows nothing about the infrastructure of what it takes to deliver those electrons and photons to a desktop. No need, we can have contractors do that. At least until you get the bill.
After 911, as only one of three Federal Civilians, I sat in a briefing room chock a block full of Generals and Colonels. They were all complaining about the cost of contractors and how ops were being delayed because they couldn't find qualified contractors. At least until I stood up and said something.
They got what they wanted. They said nothing when engineering support and technical units were being slashed in the 1990's. You can't force civilians to go into war zones. This was exactly what will happen if they had thought things through. Contractors in war zones are going to cost a lot for insurance and for the RISK. They don't work for free and you can't make them volunteer.
Even for Federal Civilians – we don't get VA or purple hearts. We get an even crappier deal now than the contractors. They get paid more and have better insurance.
All because Officer corps since 1992 doesn't know crap about how to really resource a war or build an air base. They are experts in their own little blindered world with a shallow depth of knowledge and experience.
Our pilots today can't fix a single thing on their own planes. We have “Radio Techs” coming out of our A-Schools who can't solder or know how to tell when the Built-In-Test unit is lying to them.
A whole pack of nearly useless button-pushers. The cyberwarfare is the worst pack of button pushers.
The Communications career field across the DoD is collapsing and the officers think it is all hunky-dory because their power point slides say it is.
How do you recruit techno-wizards from Colleges into the Cyberwarfare or Communications communities when it takes a week to plunk a pathetic $500 (commercial retail) Standard Desktop PC or laptop in front of them that the Standard Systems Group (SSG of Gunter) paid $1200 USD for. Then on top of that what is loaded is all Microsoft software and no end-user privileges.
Crippled hardware, crippled software and a poor understanding of real cyber-defense. That is the clear message given from week one.
If they handed out awards for who could stick their heads the furthest up Microsoft's rear-end while paying them $500M each year for what any other company would have paid $56M for… The USAF, Navy, and Army would win hands down.
Another useless training curriculum and a cyber patch won't solve the DoD's problems. These problems have been two decades in the making and I haven't met a man or women in uniform in the last six years that earned my respect. So no cajones, no fixing these problems.
We don't need hanger queen airplanes just so General and Colonels can have a cushy slot somewhere (B-1, F-22 and F-35).
That is why the Undersecretary for Personnel gave a speech three weeks ago complaining about their lack of ability to retain engineers, scientists and computer specialists (hackers and IT pros).
Here is a little known send off for you. Did you know that as of last week, the last Engineer in the entire USAF who was an Air Traffic Control and Aircraft Landing Systems (ATCALS) expert retired. There is no one behind him in training or OJT.
You would think that the USAF brass, since they own airplanes would want a few ATCALS engineers around (not just a ATC controller or Radio Tech). This crap costs millions to purchase and install. You need real experts to run the cost estimates, project plans, the contracts and the QA.
No he retired because if he had stayed in, he would have been forced to become a Cyberwarfare IP bit-head (a derogatory term for computer button pusher hackers, who are mostly 13 year olds or who act like them), which to him is not real engineering and not what he wanted to do. So he retired early and has no intention of working as a DoD contractor.
Who they gonna call when the next TACAN or VORTAC or ILS or Radar goes down and requires replacement?
They're gonna call their pack of TCP/IP cyberwarrior button pushers who are going to say, what's that?
Over the past decade I've heard the complaints of plenty of young college graduates who came into the DoD and became disillusioned by the poor networks, the poor computers, the locked down nearly useless software, the even poorer servers. They stay in just long enough to meet their commitment for how they were recruited and then they are gone.
I can”t blame them. I even punched out last year.