See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
This is where plain JPEGs are placed for public use as desired, under Creative Commons copyright with commercial restriction.

See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

Robert Garigue was focusing only on the “technical” side of the matter. The above divide is compounded (made exponentially worse) by the divide between cyber-services and human end-users. To the best of our knowledge, no one has done a full-up functional requirements survey since 1986, and we still do not have the eighteen CATALYST functionalities in a single integrated software tool-kit because no managers are ever held accountable for failure, nor do they hold vendors accountable for delivering vapor-ware rather than functionality.

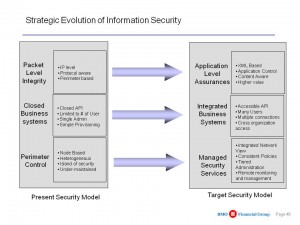
Core Point: The US national security world is still operating under a two conflicting paradigms: stovepipes within which authorized users have access to everything in the stovepipe (more or less); and isolated stovepipes in which external authorized users have to spend 25% of their time gaining access to 80+ databases (or worse, don't bother), and if they forget their password, a 2-3 day gap while access is restored. What SHOULD have happened between 1986 when this was first pointed out and 1994 when the national alarm was sounded, was full excryption at rest of all documents, and a combination of automated access roles and rules together with anomaly detection at any point in the system including external drives. The good news: 90% or more of what needs to be shared is NOT SECRET. Bad news: someone other than the US Government “owns” that 90%. The US system is not capable of ingesting and then exploiting that 90%.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

Core Point: Information Security must enable both risk and advance–for example, M4IS2 (multinational, multiagency, multidisciplinary, multidomain information-sharing and sense-making). Today cyber-security is an OBSTACLE to progress because it is, in one word, retarded–in two-words, risk-averse rather than risk-bounding.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

Credited by Robert Garigue to Gabe Davids of EDS.
Core Point: Done properly, security enables MORE risk-taking, allows one to do MORE with LESS. In other words, cyber-security policies that are risk-averse instead of risk-enabling are, in a word, retarded and retard the enterprise. Case in point: Wikileaks leading to no more flash drives–what SHOULD be in place is all the flash drives one wishes, but embedded security that prevents or flags abuse of those flashdrives.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

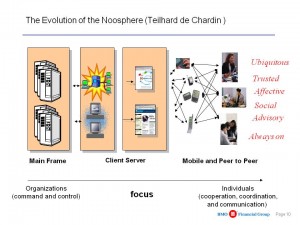
Core Point: It is not possible to have centralized cyber-anything if both the human end-users and all of the (multi-media and multi-lingual) data is distributed. This is especially true of security, which is historically several steps behind mission area processes to begin with, and any form of top-down “regulation” that tends to appear after the fact rather than “just in time.”
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing