
The author is a US Army Col who retired to Italy in 1996. He has written prolifically for the past thirty years and remains active in various informal capacities.

24 Dec Journal: Get America Working–A Conversation
3 Jan Journal: Get America Working–A Conversation Part II
Andrew Carpenter responds (Robert Steele's opening at end):
I offer here a cautionary note in three areas.
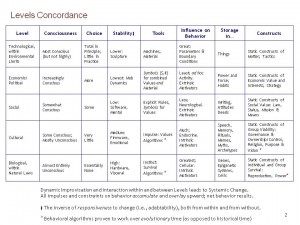
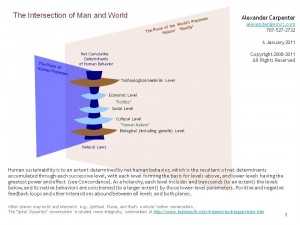
First, Robert, I get that you have a prior commitment to electoral reform, and that's your proprietary thing close to your heart. I note that when you write about it, when you present its rationale and its principles, they are cast in terms of values that are rooted in culture. Your overriding conversation is cultural; yet the proposed solution is social. There is a distinct layering of effective content and influence in our human world; without understanding that layering one is lost at trying to make sense of that world. That is one reason (of many, but this dissonance is fundamental) so many would-be “change agents” are so ineffectual.
To begin to try to start to introduce you to entering into an initial exploration of what in conventional Cartesian terms is a hierarchy of powers (but which is is actuality a holarchy), I am attaching a file that is not a literal sequential exposition of that holarchy (and I recommend you look up that notion for starters, as it is one of the conceptual keys to liberation from our conditioning), a pointillistic file that is a series of illustrations and reminders of structural relationships to support an actual internal conversation in mental-and-emotional real-time, and not a lesson in and of itself. It has not the slightest pretension to being complete. The concepts therein are a visitation from a different paradigm, and cannot be learned through reasoned discourse from within our established mental frameworks, only experienced gradually such that the old paradigm is subsumed into a larger awareness that leaves it behind like counter-intuitive Einsteinian relativity and quantum physics have “left behind” the more-mechanistic and less-sublime Newtonian and Cartesian world-view.
The reason I distinguish between the cultural and social levels in this context is that making new rules (social level) won't change people's net overall behaviors, only new core motivators (cultural level) will. After all, the old rules haven't worked in our present configuration, why would just changing to new ones work without other shifts? New rules alone is like putting lipstick on a pig, like building a house on sand, and a classic case of legislating (a social tool) morality (cultural values). Famous, in all cases, for not working, as values (for good or for ill) will always find a way around, under, over, or directly through rules. We've seen it a gazillion times.
Continue reading “Journal: Get America Working–A Conversation Part III”

Table of Contents
Key Judgments & Recommendations
Background
Internet Facilitated Organized Crime
Challenges and Opportunities
Emerging and Future Trends
Concluding Remarks
Phi Beta Iota: The most interesting aspect is the recognition that neither government nor corporations nor social networks can be safe in isolation–there is a clear and compelling requirement for new forms of hybrid multinational information-sharing and sense-making networks, protocols, and combinated coalition threat studies and capabilities.

More jerks advocating their wares….I have taught since the mid 1990's that the greatest threat to computer security was the insider. On one hand He/She has access and only need motivation to become hostile. On the other hand, slovenly attitudes allow others, without access but motivation, to take advantage of the insider…..now all of a sudden it seems to be the great revelation…..and somewhat ties into Secrecy News release today about the leaking of information to a news reporter……
Phi Beta Iota: We will not dignify the vendor that inspired Brother DefDog's rant with a mention or link. Yes, the insider can do the most damage. Yes, modest internal measures can be taken (such as CIA finally got around to and DoD still cannot implement because of its decades of out of control cyber-archipelago private gardens). Two major points are still not understood by those who would be cyber-commanders:
1. No amount of tactical diligence can make up for strategic folly. When you have both a global and a domestic governance program that is out of control and obviously against the best interests of the public, this is going to inspire internal leaks that cannot be stopped.
2. Errors and omissions–bad design, bad acquisition, bad management–are made worse by excessive investments in information technology to the detriment of education and embedded human integrity. Paul Strassmann said this, Mich Kabay said this, both in the 1990's, and we still don't get it.
Journal: Army Industrial-Era Network Security + Cyber-Security RECAP (Links to Past Posts)
Journal: Cyber-Idiocy Wipes Out Productivity
Journal: Reflections on Integrity
Journal: WikiLeaks Collaboration, WikiLeaks Attacked + CYBER RECAP
Reference: Cyber-Intelligence–Restore the Republic Of, By, and For…