
The US IC has spent 1.2 trillion dollars since 1992 — and failed to provide ethical evidence-based decision-support capable of influencing tens of trillions more. This waste has to be understood in the context of a leadership (both intelligence and political) focused moving money, not actually in the business of producing decision-support or making decisions in the public interest.no.
All of these documented advisories were published in the key journals of the time, and ignored.
What does it say when an intelligence community is incapable of doing intelligence on itself?
DOC (1 Page Table): Steele On Intelligence Cross-Walk Over Time
Extracts (quotes on NSA not in table) and Links Below the Line
2010 OPINION–America's Cyber Scam (Homeland Security Today)
I am quite certain that a careful examination of all extant SOWs would reveal a degree of obscurity and incoherence confirming that the US Government is engaged in a massive collective self-deception and entertaining bids for vaporware amidst a climate of fear, uncertainty, and doubt (FUD), the latter a tactic of rhetoric and fallacy used in sales, marketing, public relations, politics and propaganda.
In my judgment, informed by consultation with a few colleagues and a simple review of the open record, there are fewer than 100 people in the USA who could be called legitimate cybernauts and are qualified for appropriate security clearances.
– – – – – – –
Way back in 1994, however, joining with several others, I called for $1 billion in cybersecurity investments – roughly the equivalent of the $12 billion that’s been proposed by the administration. If there’d been enough foresight and fortitude on the part of policymakers a quarter century ago to begin taking action then when those of us who were aware of the looming cybersecurity risks were screaming about the clear and present need to do something, we would have gotten a substantially broader, deeper and more timely return on investment (ROI).
At the same time, I personally introduced the government to its own hackers beginning in 1993 when the National Security Agency (NSA), at my invitation, sent two busloads of employees down for a special encounter with Hackers on Planet Earth and the 2600 Hacker Quarterly gang from New York—pioneers with the right stuff you simply could not then, and cannot now, learn in school.
– – – – – – –
We have wasted 25 years—a quarter century. It is time for a reassessment.
The US Government thus is about to blow $12 billion dollars it can ill-afford on mission impossible: achieving cybersecurity in the absence of everything needed.
– – – – – –
In my view, NSA is now a negative factor against national security and national prosperity because NSA thrives on cyber-vulnerabilities and compels corporations to aid and abet. NSA is giving the Chinese and the Israelis, the Germans and the French, and all others, free access to all our systems because NSA would rather that we remain vulnerable so they can have a big budget, instead of making NSA irrelevant by creating anonymous peer-to-peer computing and communications that are impervious to intercept.
Activate the “M” in OMB, doing Whole of Government strategic presidential management
Reinvent concept of national security
Fixing the WH
• Deputy VP for Commonwealth
• Deputy VP for National Security
• Director-General for Global Strategy
• Convert NSC into a National Policy Council
Fixing Intelligence
• Embrace the Strategic Analytic Matrix – ten high level threats, twelve core policies
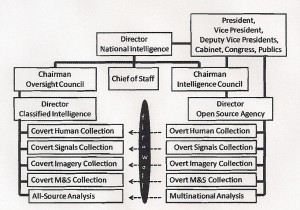
• Create Open Source Agency
• DCI as Director of Classified Intelligence
• Integration of education, intelligence, and research
• Global Range of Needs Table
2009 Intelligence for the President–AND Everyone Else (CounterPunch)
Among those remaining in power are LtGen Keith Alexander, USA, who covered up and destroyed the ABLE DANGER discovery of two of the 9-11 terrorists prior to 9-11, rather than share them with the FBI. This is the same person who wants $12 billion dollars to achieve cyber-security, but who will actually use that money to assure digital nakedness for every single person, thing, and datum. I do not trust him.
2009 Intelligence for the President–AND Everyone Else (CounterPunch)
Create Open Source Agency as recommended by 9/11 Commission
– with diplomatic Office of Information Sharing Treaties and Agreements
– with a Multinational Decision Suppoirt Center and Network
– Funding a Community Decision Support Networks
2002 The New Craft of Intelligence–What Should the T Be Doing to the I in IT? (to NSA in Las Vegas)
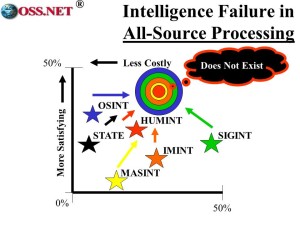
The information we do collect never gets processed in an integrated way. At the same time, our analytic toolkits–including tools for collaborative work across organizational boundaries–are a disgrace, mostly because management has never been willing to reduce spending on collection technology is order to create analysis technology.
We must have a single integrated all-source processing agency to make sense of it all and we must have toolkits.
If we apply the “T” to these two challenges, we increase IC productivity by a factor of at least 10, perhaps 100. In combination, “TC” and “TP” = an IC 100X better.
– – – – – – –
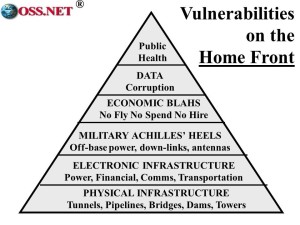
This is an illustration of the various levels of vulnerability, from the physical through the electronic to the ultimate heart of America, our public health.
The center of gravity for homeland security is in the private sector, and this is going to require some major conceptual, doctrinal, financial, and force structure trade-off decisions, even as DoD again accepts responsibility for homeland defense.
– – – – – – –
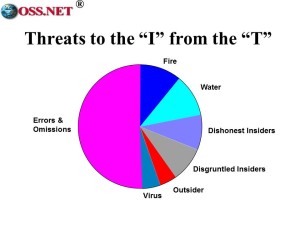 As I begin my technical conclusion, I want to start with some rough estimates about sources of loss within computer systems & data. Badly devised “T” is a much greater threat to the “I” than deliberate attack.
As I begin my technical conclusion, I want to start with some rough estimates about sources of loss within computer systems & data. Badly devised “T” is a much greater threat to the “I” than deliberate attack.
We lose half the value of our data to errors and omissions caused by mediocre data ingestion programs. You’re off the hook on the 20% lost to fire and water–that’s simply bad management, with either no data back-up or data back-up files stored in the same room as the core data files.
Dishonest and disgruntled insiders do the most deliberate damage, in part because our systems are generally not designed to detect authorized users doing unauthorized things. Only at the very end do we see viruses, many of which arrive in shrink-wrapped factory software and hardware, and outsider attacks. The bulk of our technical threat is one of our own making.
2002 THE NEW CRAFT OF INTELLIGENCE: Personal, Public & Political (Chapter 15)
001 Decision-Support Raison D’être
002 Value-Added from Analysis
003 Global Coverage Matters More
004 Non-Traditional Threats Tops
005 Intelligence w/o Translation is 0
006 Source Balance Matters More
007 “Two Levels Down” (to Street)
008 Processing Matters More
009 Cultural Intelligence Vital
010 Geospatial and Time Tagging 011 Global Open Source Baseline
012 Counterintelligence is Root
013 Cross-Fertilization Matters
014 Decentralized Intelligence Core
015 Collaborative Work and Informal Communications Rise
016 New Value is in Content + Context + Speed
017 Collection Based on Gaps
018 Collection Doctrine Nuances
019 Citizen “Intelligence Minutemen” are Vital
020 Production Based on Needs
021 Strategic Intelligence Matters
022 Budget Intelligence Mandatory
023 Public Intelligence Drives Public Policy
024 Analysts are Managers
025 New Measures of Merit
026 Multi-Lateral Burden-Sharing is Vital
2000 ON INTELLIGENCE: Spies and Secrecy in an Open World (Chapter 13)
10. Encryption. NSA is still seeking to limit private sector encryption and to negotiate secret back doors with major vendors of computing and communications equipment. This dog will not hunt. In the age of information, the center of gravity for both national security and national competitiveness is in the private sector, and it is the integrity of private sector communications and computing that will decide if our Nation remains the foremost global power in the 21st Century. America must be the one place in the world where smart people can develop smart ideas while being fully confident that the fruits of their labor will be protected in our electronic environment. We must not handicap and seek to penetrate our own business software—to do so is to undermine our own national security and national competitiveness.
2000 ON INTELLIGENCE: Spies and Secrecy in an Open World (Chapter 13)
1. Establish a National Information Strategy
2. Undertake a Digital Marshall Plan
3. Refocus education on individual education and family integrity
4. Create both a DGNI and a Director of Public Information
5. Create the Technical Collection Agency
6. Elevant the NIC to the Office of the DGNI, expand to 60 seats
7. CIA to be National Analysis Agency
8. Earmark $1 Billion a Year for Open Sources
9. Bring together all eight information tribes
10. Replace spies in Embassies with inter-agency analysis teams
11. Create global extranet for peacekeeping intelligence
12. Create an FBI division dedicated to business protection
13. Stop NSA from handicapping encryption
14. Stop covert action
Communications & Computer Security. We have a house built over a sinkhole! The vulnerabilities of our national telecommunications infrastructure to interruption of services as well as destruction, degradation, and theft of data are such that experts feel comfortable in predicting that–unless we are able to establish a major Presidential program in this arena–we will see a series of enormously costly electronic attacks on our major financial and industrial
organizations, generally undertaken by individuals who stand to benefit financially from degraded or interrupted performance. The current generation of systems engineers was not raised in an environment where security was a necessary element of design. At every level, through every node, we are wide open–and in a networked environment, one open house contaminates the next.
1994 Sounding the Alarm (Letter to Marty Harris, Department of the Treasury)
We are also politically handicapped because those that do understand these matters generally conceal their losses and/or hide behind a
classified compartment. As one of those testifying to the Committee noted (I believe he was a former National Security Agency officer), it is both a political and an economic mistake to classify the C4 threat, for it prevents public and legislative understanding of the
magnitude of the threat, and the urgent need for concerted action across both government and private sector lines.
When Tom Clancy is so bold as to write about the electronic melt-down of Wall Street (my friend Winn Schwartau's novel Terminal
Compromise may well have provided Clancy with his ideas), we have a problem that needs Presidential leadership. It is time for us to shed some light on the fact that we have a house built over a sinkhole, and resting on nothing more than an egg-shell of badly engineered systems (including the planned NII backbone).
1992 AIJ Fall ‘New Paradigm” and Avoiding Future Failures
1. Excessive collection of technical intelligence
2. Cursory attention to both open source collection, and the need for a modest expansion of our clandestine human collection capability
3. Severe shortcomings in control over intelligence resources – no capability to evaluate relative returns on investment
4. Mindset inertia – two generations away from understanding Third World and low intensity challenges; entire structure does not lend itself to being restructured
5. Lack of accountability among acquisition managers and the intelligence professionals who support them
6. Lack of commitment to people
1990 Intelligence in the 1990′s – Six Challenges
1. Meeting Needs of Public Programs
2. Indications & Warning for New Threats (i.e. Revolutionary Change)
3. Theory & Methods for Counter-Intelligence and Operations Security
4. Information Technology Strategy
5. Establishing a Responsive Requirements System
6. Realigning Resources in an Era of Radical Change
See Also:
2014 Rethinking National Intelligence — Seven False Premises Blocking Intelligence Reform
2014 Intelligence Reform (Robert Steele)
Graphic: A Short Story-Terrorism as a Boil
Robert Steele Biography & Linked Publications



