See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

Robert Garigue was focusing only on the “technical” side of the matter. The above divide is compounded (made exponentially worse) by the divide between cyber-services and human end-users. To the best of our knowledge, no one has done a full-up functional requirements survey since 1986, and we still do not have the eighteen CATALYST functionalities in a single integrated software tool-kit because no managers are ever held accountable for failure, nor do they hold vendors accountable for delivering vapor-ware rather than functionality.
By Shane Harris sharris@nationaljournal.com April 4, 2007
Government Executive
In 1999, program managers at the National Security Agency knew they were in trouble. A new and important electronic filtering system, code-named Trailblazer, wasn't working as designed.
Planners imagined it would automatically find phone calls, e-mails and electronic communications of terrorists and other threats sitting in NSA's massive intelligence haul. But Trailblazer was coming unglued before it was out of the gate.
Rather than pull the plug, for six years the agency tried to save Trailblazer, transferring management responsibility to different teams that tweaked the design and made it more complicated. Like some toxic jug of moonshine, Trailblazer was passed around among agency and contract personnel until, $1.2 billion later, it still didn't work.
This story of massive failure came to light through the dogged reporting of The Baltimore Sun‘s Siobhan Gorman, who is deeply sourced on NSA issues. In February, she revealed that yet another data-sniffing project was under way. Aptly named Turbulence, it, too, is on the rocks, with annual costs approaching $500 million.
If you're shaking your head, it's probably because you know the Trailblazer story isn't unique. The FBI, the Internal Revenue Service and the Marine Corps, to name a few, have watched massive system modernizations crash and burn. The reasons for these disasters are well-documented and maddeningly similar: insufficient agency management, contractors that overpromised and anemic-to-nonexistent congressional oversight.
. . . . . .
This all sounds cynical, because it is. Whether or not it's deliberate is another matter. But you don't have to believe that people consciously fail to recognize the windfall it brings. Even if they don't know why, there's a reason people keep making the same mistakes: Failure is one of the most successful things going.

Seminal Technical Preface (2008)
Gunnar Peterson on Robert Garigue’s Last Briefing
Core Slides as Expandable JPEG with Comments:
Robert Garigue: When Everything Else is Distributed….
Robert Garigue: Information Security MANDATE
Robert Garigue: Structuring Risks (Role of Security)

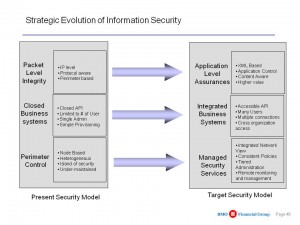
Core Point: The US national security world is still operating under a two conflicting paradigms: stovepipes within which authorized users have access to everything in the stovepipe (more or less); and isolated stovepipes in which external authorized users have to spend 25% of their time gaining access to 80+ databases (or worse, don't bother), and if they forget their password, a 2-3 day gap while access is restored. What SHOULD have happened between 1986 when this was first pointed out and 1994 when the national alarm was sounded, was full excryption at rest of all documents, and a combination of automated access roles and rules together with anomaly detection at any point in the system including external drives. The good news: 90% or more of what needs to be shared is NOT SECRET. Bad news: someone other than the US Government “owns” that 90%. The US system is not capable of ingesting and then exploiting that 90%.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

Core Point: Information Security must enable both risk and advance–for example, M4IS2 (multinational, multiagency, multidisciplinary, multidomain information-sharing and sense-making). Today cyber-security is an OBSTACLE to progress because it is, in one word, retarded–in two-words, risk-averse rather than risk-bounding.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing