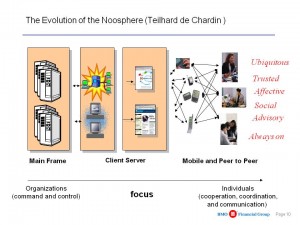
Core Point: The US national security world is still operating under a two conflicting paradigms: stovepipes within which authorized users have access to everything in the stovepipe (more or less); and isolated stovepipes in which external authorized users have to spend 25% of their time gaining access to 80+ databases (or worse, don't bother), and if they forget their password, a 2-3 day gap while access is restored. What SHOULD have happened between 1986 when this was first pointed out and 1994 when the national alarm was sounded, was full excryption at rest of all documents, and a combination of automated access roles and rules together with anomaly detection at any point in the system including external drives. The good news: 90% or more of what needs to be shared is NOT SECRET. Bad news: someone other than the US Government “owns” that 90%. The US system is not capable of ingesting and then exploiting that 90%.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing