PDF: 1999 Setting the Stage for Information Sharing in the 21st Century
Reference: 1996 Hill Testimony on Secrecy
Hill Letters & Testimony, Memoranda, Secrecy & Politics of Secrecy
We must “recognize that 80% of what we consider intelligence–decision-support–is now either erroneously classified or not done at all, and this is the fundamental weakness of our national intelligence community.
The three references:
1996 Testimony to Moynihan Commisson
1993 TESTIMONY on National Security Information
1992 E3i: Ethics, Ecology, Evolution, & intelligence (An Alternative Paradigm)
Reference: 1996 Testimony to Moynihan Commisson
Hill Letters & Testimony, Memoranda, Secrecy & Politics of SecrecyAs Presented:
OSS1997-03-03 Secrecy Primer Moynihan Commission
The protection of “sources & methods” is a political gambit, not a legitimate claim for immunity. This testimony to the Moynihan Commission on Secrecy lays out the hypocricy in detail.
See Also:
1992 E3i: Ethics, Ecology, Evolution, & intelligence
RELATED:
Worth a Look: Books on Government Secrecy
Reference: 1995 Bill Gates Internet Tidal Wave Memorandum
Memoranda
Phi Beta Iota: Although labeled Confidential the document that we link to is publicly available at the US Department of Justice web site. Below is a summary of what we took away from this document, which was prescient by most standards (www.oss.net was created in 1993 by Dr. Eric Thiese, then the Internet Editor for WIRED Magazine).
Early points of interest to Bill Gates:
01) Scale to Infinity and Beyond
02) Traffic volume and speed
03) Content enhancement including 3-D visualization
04) Marginal cost of added communications use zero
05) Content-user feedback loops create the tidal wave
06) Client services must follow, help create and publish on the web
07) Technical Challenge: Real-time content
08) Technical Opportunity: Human in the loop on tap 24/7
09) Open source alternatives to the commercial internet “scary”
Internal Action Areas Identified by Bill Gates:
01) Servers
02) Client PC's (Internet would extend life of PCs)
03) File Sharing
04) Forms/Languages
05) Formats
06) Tools
Areas for Immediate Consideration:
01) Office on to the Internet
02) MSN scaling up
03) Broadband media
04) Electronic commerce
Cool Reference:
Application Strategies for the World Wide Web by Peter Pathe
Internal Challenge:
Coordinating various development activities across a very large complex global enterprise
1994 Sounding the Alarm on Cyber-Security
Correspondence, Memoranda
This is the cover letter to the US Government official most responsible for thinking about the National Information Infrastructure (NII) and the security of that infrastructure. Three “top guns,” one of the the foremost authority in the public arena, another the foremost expert on these matters advising the National Security Agency (NSA) all agreed on the need, in 1994, for a $1 billion a year program.
Today (Fall 2009) NSA has asked for $12 billion a year, and they are not letting on that the real reason they are building their own power plant is because the Chinese have mastered the art of riding the public electrical grid into any computer running on public electricity. Below are the cross walk and the contributing letters from the top experts in 1004. NSA has let us all down.
UPDATE OF 19 DECEMBER 2016:
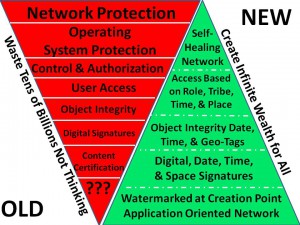
Both Bill Caelli and Winn Schwartau have new books coming out in 2017, the bottom line of which is that we can indeed secure cyberspace, but it requires that governments and the providers of communications and computing software and hardware have integrity — not the case today. Below is the concept Robert Garigue (RIP) and Robert Steele developed in 1997. No one has implemented this to date.
1993 Talking Points for the Director of Central Intelligence
Correspondence, Memoranda
This was faxed to John Deutch when he was DCI. It probably made it to his desk only to be dismissed as it was not from anyone remotely associated with power or money. This was the beginning of our realization, articulated in 1997 for the US Institute for Peace, that those with power know too little, and those with knowledge have no power.
Since then we have also determined that too many senior executives in both government and business leave the sorting of incoming mail to interns and the lowest paid receptionist–there is no “intelligence” at the front end of the enterprise that can identify and flag “weak signals.”
Even when writing to the top 2000 people in America across roughly 15 segments, we discovered that even the most sensible attempt to engage, absent a “hook” that is already entrenched, tends to fail.
DOC (9 Pages): 1993 Steele Fax to DCI John Deutch
Full Text Below the Fold
Continue reading “1993 Talking Points for the Director of Central Intelligence”
1992 Information Concepts & Doctrine for the Future
About the Idea, Memoranda, White PapersPDF: 1992 Information Concepts & Doctrine for the Future
Full Text Online Below the Fold
Continue reading “1992 Information Concepts & Doctrine for the Future”



