Original (Web): INFORMATION WARFARE – Developing a Conceptual Framework
Copy (Document): INFORMATION WARFARE – Developing a Conceptual Framework
Original (Web): INFORMATION WARFARE – Developing a Conceptual Framework
Copy (Document): INFORMATION WARFARE – Developing a Conceptual Framework
Below is secured for the future. As of 24 December 2010 it is still online at Carleton University. Dr. Robert Garigue passed away 10 January 2007 at the age of 55. He was the only person we knew then or know of today that was deliberately and completely integrating belief systems, knowledge, information, data, security, and technology as a single cyberspace.
Continue reading “Robert Garigue: Carleton University Research Page”
Information security is not a static process–you cannot “lock down” information the way the Air Force has tried to do, prohibiting all flash drives because it has failed over decades to actually embed security in every aspect of the process from human to download alerts. Interactive feedback loops are simple and effective. Winn Schwartau pioneered time-based security and risk-based security. Now if we just accept the fact that 80% or more of the information we need to be effective is not secret, not in English, and often not online at all, this represents a 180 degree turn away from the current focus on centralized cyber-security to the exclusion of all else (such as mission effectiveness). As Russell Ackoff put forward: we have been doing the wrong thing righter, and are about to spend $12 billion doing the wrong thing righter, instead of going ALL STOP and redesigning all systems, human to technical, around M4IS2 (multinational, multiagency, multidisciplinary, multidomain information-sharing and sense-making). One can no more merge all the Serious Games into one World Game than one can merge all the stovepipes into one “all-source” system. We have to do a clean-sheet requirements review and design for M4IS2 success, otherwise we automatically default to more of the failures that NSA and its various contractors are so notorious for….
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

IMPORTANT: The Chief Information Security Officer (CISO) is not the Chief Knowledge Officer (CKO) nor the Mission Commander or the Mission Logistics Officer or any of the other mission support specialties. The point is that security and knowledge must co-exist and in collaboration with one another, the CISO and CKO need to ensure that the force is trained, equipped, and organized so that the right information is available to the right person at the right time in the right format. If in doubt, err on the side of access, not control. It is much easier to do that if you are honest about NOT classifying the 80% that should NOT be classified.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing

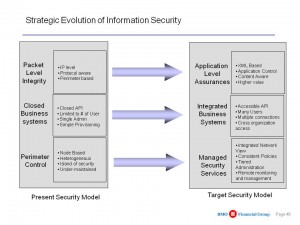
Robert Garigue was focusing only on the “technical” side of the matter. The above divide is compounded (made exponentially worse) by the divide between cyber-services and human end-users. To the best of our knowledge, no one has done a full-up functional requirements survey since 1986, and we still do not have the eighteen CATALYST functionalities in a single integrated software tool-kit because no managers are ever held accountable for failure, nor do they hold vendors accountable for delivering vapor-ware rather than functionality.

Seminal Technical Preface (2008)
Gunnar Peterson on Robert Garigue’s Last Briefing
Core Slides as Expandable JPEG with Comments:
Robert Garigue: When Everything Else is Distributed….
Robert Garigue: Information Security MANDATE
Robert Garigue: Structuring Risks (Role of Security)