Military Archives on Public Intelligence (1992-2006)
Military

In my view, books like this as well as the non-fiction books such as “Information Warfare: Chaos on the Electronic Superhighway” have been vital elements in educating consumers, stockholders, and voters. If you want to know just how vulnerable your bank account is, read this book.
I won't reveal the surprise ending, but will say that it is absolutely a shocker, and totally credible.


This is the cover letter to the US Government official most responsible for thinking about the National Information Infrastructure (NII) and the security of that infrastructure. Three “top guns,” one of the the foremost authority in the public arena, another the foremost expert on these matters advising the National Security Agency (NSA) all agreed on the need, in 1994, for a $1 billion a year program.
Today (Fall 2009) NSA has asked for $12 billion a year, and they are not letting on that the real reason they are building their own power plant is because the Chinese have mastered the art of riding the public electrical grid into any computer running on public electricity. Below are the cross walk and the contributing letters from the top experts in 1004. NSA has let us all down.
UPDATE OF 19 DECEMBER 2016:
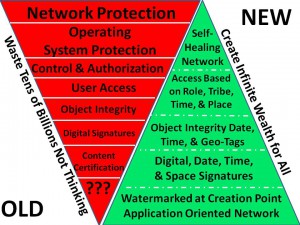
Both Bill Caelli and Winn Schwartau have new books coming out in 2017, the bottom line of which is that we can indeed secure cyberspace, but it requires that governments and the providers of communications and computing software and hardware have integrity — not the case today. Below is the concept Robert Garigue (RIP) and Robert Steele developed in 1997. No one has implemented this to date.