
Winn Schwartau
6 Stars – Foundation for IT & Web 3.0 Security
This book is critical to the post-Western Web 3.0 new Internet and should be translated into Chinese and Russian as soon as possible.
This is a Nobel-level piece of work that provides everything that Vint Cerf and Tim Berner-Lee failed to plan for. It exposes the IT industry for the insecure naked posturing ponzi scheme that it is.
Winn recommends, and I agree, Norbert Weiner's Cybernetics as his own inspiration. I would rate Winn's contribution at this time as the equal of Weiner's radical break-out book but would add Peter Corning's 2009 book on Holistic Darwinism, and others that can be found at the link for Cybernetics @ Phi Beta Iota. Winn's focus is on improving the security of online information, not on improving the collection, processing, and sharing of substantive intelligence (decision-support) across all subject matter domains.
I have known Winn Schwartau since we co-founded InfoWarCon under his leadership — I dropped out early to focus on my own event focused on Open Source Intelligence (OSINT) — and have always been delighted that Winn was one of the three co-authors with me of the first warning letter to the White House in 1994 on cyber-vulnerabilities (afterhis being the first to brief Congress on the inevitable “electronic Pearl Harbor”).
Steele, Robert with James Anderson, William Caelli, and Winn Schwartau, “Correspondence, Sounding the Alarm on Cyber Security,” McLean, VA: Open Source Solutions, Inc., August 23, 1994.
 Winn — who gives credit in this book to Bob Ayers on one end (1995) and Mark Carney (the math, 2018) on the other end– is the Top Gun on this topic, and has the patents in hand to execute. What is NEW is that his ideas are fully documented with mathematical proofs of viability and value, and the book is a work of art with images and graphics and overall composition worthy of being placed in the Smithsonian just as Winn himself should one day be featured at Madame Tussauds (the wax museum not the whorehouse).
Winn — who gives credit in this book to Bob Ayers on one end (1995) and Mark Carney (the math, 2018) on the other end– is the Top Gun on this topic, and has the patents in hand to execute. What is NEW is that his ideas are fully documented with mathematical proofs of viability and value, and the book is a work of art with images and graphics and overall composition worthy of being placed in the Smithsonian just as Winn himself should one day be featured at Madame Tussauds (the wax museum not the whorehouse).
I recommend this book for corporate leaders who need to know just how vulnerable they are not being told they are; for IT managers that might wish to get it right; for insurance companies that might wish to radically improve their odds of avoiding catastrophic losses because their definition of “due diligence” is retarded; and for faculty, students, and wonks, who would like to avoid a total meltdown of the 21st Century's infosphere. The hackers and crackers already get all this — they get in and out in seconds, hours, days, while IT “security” focuses on ineffective protection and leaves detection and reaction to days, weeks, and months. Time is not only a strategic variable (it cannot be bought nor replaced) it is a tactical variable — if the attacker works in seconds and you work in any longer span, you are lost and will remain lost.
The book can be read in an afternoon but will reward subsequent readings. This review is an executive summary, but no substitute for most extraordinary composition I have read in this field since I was a co-founder of CIA's Artificial Intelligence Staff in 1986, and then the Marine Corps Intelligence Activity (MCIA) and the modern discipline of Open Source Intelligence (OSINT) in 1988. Paul Strassman in Information PayOff spoke to the failure of digital delivery in relation to books when considering hand-eye coordination and the physical manifestation of the knowledge.
This is three books in one — the core common sense ideas that are indiputably an indictment of the IT industry today as well as all corporate CEOs tolerating a retarded ineffective security paradigm; an extraordinary museum-quality integration of graphics and photographs and design that is out of this world; and mathematical formulas and charts that leave me cold but will impress the geeks. All that matters for me is that I trust Winn to be right, 100%.
I learn in passing that he grew up with Richard Stallman, one of my other heroes and the founder of the Free/Libre/Open Source Software (FLOSS), movement, Richard and I have come up together, I founded OSINT at the same time that he was pioneering GNU and founding the Free Software Foundation.
Let me start by honoring Robert Garigue, whom Winn and I both admired deeply and whose work continues to be fundamental despite his early demise. Robert and I created the below graphic in 1997 and could never get our respective governments to understand that they were doing it all wrong and needed to kill centralized security, what Winn calls “root” and completely redesign how we embed security in the actual data.
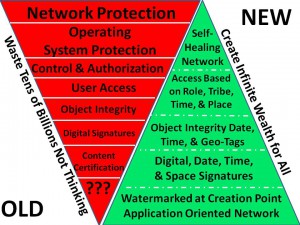
Note especially Access based on Role, Tribe, TIME, & Place. Security is contextual. Winn gets this, I get this, most people do NOT get this because they are lazy and are not held accountable for real-time and near-real-time digital security including monitoring of the human gatekeepers that are too easily social engineered. Side note: when Winn and I spoke at Hackers on Planet Earth (HOPE) in 1994, a hacker on an open speaker phone social engineered the phone company's technical support element into giving them root access, in front of a plenary standing room only crowd with the phone company vice president in the front row. The hacker introduced himself to the phone company data tech as Dave from the Department of Social Engineering. Nothing has changed in all these years.
Core Point: Everyone is building Maginot Line fixed defenses and not focusing on the need to do real-time and near-real-time detection and reaction. The industry standard is still in the daily to weekly audit trail review. The harm that can be done in a fraction of the time before stakeholders notice the break and entry is colossal.
Core Point: Two-Man Rule over root changes (before we can get rid of root) radically increases security. However, trust is contextual, changes at the individual level depending on task and timing, and the more people have any kind of root admin authority, the more likely the system is to collapse.
Core Point: security companies are not guaranteeing their products; are not providing time-based efficacy certifications; and even at the accepted failure rate, are allowing thousands of forbidden accesses and dangerous phishing links into every major system every single day.
Core Point: security evolves much more slowly than the hardware and software it is supposed to be protecting.
QUOTE (12): For all practical purposes our approach to computer and network security has been static and limiting.
To which I would add, and not in the least bit accountable.
Winn identifies nine qualities of effective network security on pages 18-19: simplicity, utlity, scalable, measurable, quantifiable, provable, supports management, brings risk to the table, adds value.
Core Point: each aspect of security done in depth and breadth BUYS TIME to DETECT and REACT.
QUOTE (38): if the measured time afforded to me by a protection device is greater than the amount of time it takes to direct and respond to (repair, halt) an attack, then I have a secure environment.
Core Point that I remember discussing in the 1990's: it is insanely expensive and ineffective to apply security measures for the highest level of protection (e.g. TS/SCI) to ALL of the information (e.g unclassified). At some point there needs to be a triage that sharply limits in an isolated separate network, that which is most sensitive.
To this I would add that almost everything that is TS/SCI is overly classified and largely worthless. I still remember shredding all TS/SCI every morning as the S-1 Adjutant of Battalion Landing Team 3/4 (1976-1977) because there was nothing there of value to our battalion in that time and place. When I co-created the Marine Corps Intelligence Activity (MCIA) in 1988, same thing. The entire $100B US secret intelligence community could not provide what the Marine Corps needed in the way of strategic, operational, tactical, and technical intelligence (decision-support) because a) they don't cover the Third World shit holes where the Marines usually go and b) they could care less about defilade, 1:50K combat charts, and other essentials at the tactical level. As General Bob Scales has documented so ably in Firepower in Limited War, national and theater intelligence stink at supporting tactical fire and movement (and we will all remember Marty Hurwitz gutting tactical intelligence including collection assets to support his vision of centralized bureaucraticized theater intelligence).
Core Point: Automated responses only work if you have pre-configured signatures. The detection of new anomalies is a challenge.
Core Point: Humans are not binary, computers should not be. Trust and access and security are relative — contextual.
Core Point: Feedback matters. Feedback can also perpetuate self-actualizing cognitive bias (e.g. fake news going viral).
QUOTE (125) : Feedback should be built-in as an architectural requirement in any dynamic system, such as data and control networks. But it's not.
Core Point: until you understand how much impact a single order of magnitude change in time has, you cannot be effective in designing network security.
Core Point: Memristors will change everything. Pages 136-137 are radical.
I have a note to myself, as the creator of the #UNRIG electoral reform project, that all of Winn's thinking will be helpful to the creation of Instant Run-Off and National Polling applications that are desperately needed (they could also reinforce Thin Thread as created by Bill Binney and associates).
QUOTE (142): The time-based approval and revocation model might bring measurable degrees of stability and equilibrium to code, networks, and security, as never before.
Core point: Trust can be measured, variations in trust matter, and trust can be managed. TIME & place and CONTEXT are essential trust variables.
If there is a flaw in this book it is the tacit assumption throughout that businesses are successful because they are optimizing information. In fact they are not. They are simply not being held accountable for integrating holistic analytics and true cost economics, which means they can pass on to the consumer — and future generations — the costs of all of their mistakes including climate change and water contamination.
Core Point: TCP/IP cannot be secured — it moves both control and data over the same line and is fragile to a fault. The author proposes a satellite based out of band control overlay, and accepts TCP/IP for all its flaws, as a given going forward.
QUOTE (185): Implementing ANS Out-of-bank (OOB) signaling and contrl paths that are isolated from each other does not require any modification to TCP/IP, or face the impossible task of replacing it.
Core Point: All detection processes should be continuously tested over time, not weekly, monthly, quarterly, or annually as now appears to be the case with most networks.
QUOTE (217): At the core of Analogue Network Security is measurement. As history has shown us, cybersecurity without metrics is a fool's errand.
Core Point: Six Sigma sucks. Not even close.
QUOTE (221): We are looking for efficacy that exceed Six Sigma Measure, Analyze, Design, Verify, OODA approach used so successfully by ICS-SCADA vendors such as GE, sometimes by a factor of 106, or more.
Core Point: Most networks have such a kludge of security applications at multiple levels that they have no idea how much capacity is being consumed. When new implementations fail, it is often because security has consumed more of the capacity than anyone realized, and the bandwidth simply is not there.
Core Point: Most organizations are not organized to respond in a timely fashion to a detection. This is particularly true after hours.
Core Point: All links, all attachments, without exception, need to be scrubbed for phishing hazards. An organization is inevitably going to ingest thousands of phishing links, and is as vulnerable as its stupidest or least attentive employee.
The author is too kind to Facebook in his discussion of Fake News, and of course makes no mention of Facebook as a primary sponsor of censorship intended to deplatform those telling the truth or challenging official narratives. I continue to believe we need a national Computational Authority that can examine and certify all algorithms and block the manipulation of polls and searches that are so common under the pay to play system (Google search shows you want someone else has paid for you to see, not what is the best or most relevant result) and the Zionist censorship system managed by the Anti-Defamation League (ADL) for the Deep State.
QUOTE (243): Citing Dr. Gene Spafford: “TCP/IP was designed to be resilient under failure, not under attack.”
Core Point: We are forgetting that cyber is not an autonomous cloud — it depends very heavily on very specific undersea cables and routing centers — it depends heavily on physical wire.
Core Point: So many consumer devices — and their local ISPs — are being coopted for malware that a Big Fix is needed — something that integrates real-time testing and metrics as well as the real-time out of band information exchange that allows all ISPs to police one another and help one another contain the threat.
The conclusion of the book comes in several truly lovely bits and pieces that include a note from Dennis Groves of Open Web Application Security Project (OWASP); a deep very special never before look at the mathematics of time-based security by Mark Carney; a security management porn primer (really); a nudge toward the policy-makers that are clueless; a short section on Speed of Signal; a detailed slam on Six Sigma; and a lovely reflection on the three domains of integrated security: physical, cyber, and human. Short pieces on Artificial Intelligence, Hiring the Unhireable, and an ANS Design Tools Cheat Sheet complete the book. The latter is provided by the author for sharing PDF (8 Pages): Analogue Network Security Cheat Sheet.
This book is a collector's item as well as an art & science object, Paul's Business Value of Computers is in some ways an extraordinary complement to this book when one keeps in mind that we are still all very retarded: we process 1% of what we collect, we collect 1% of what is published which is 1% of what is written which is 1% of what is known. All this money we are spending on IT is mis-managed and not making much sense of 1% of 1% of 1% of 1% of 1%. Duh.
Now imagine if we actually wanted to share multi-lingual, multi-media information across all boundaries, and particularly among China, Russia, and the USA? Imagine if we actually wanted to create a World Brain that respected individual, organizational, and national boundaries (i.e. China can censor what it wants but we do not let the Zionists censor anything)? This is what that would look like, with all information in all languages being available ( within agreed upon anonymity, identity, privacy, and security parameters):
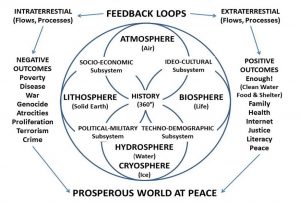
Core Point: the scale of comprehensive data digitization and sharing is EQUAL to the scale of time-based security as proposed by Winn. Web 3.0 must be a double order of magnitude improvement over the TCP/IP Balkanization we have now.
Steele, Robert. “Augmented Intelligence with Human-Machine Integrity: Future-Oriented Hybrid Governance Integrating Holistic Analytics, True Cost Economics, and Open Source Everything Engineering (OSEE),” in Daniel Araya. Augmented Intelligence: Smart Systems and the Future of Work and Learning. Bern, CH: Peter Lang Publishing., 2018.
Steele, Robert. “Foreword,” in Stephen E. Arnold, CyberOSINT: Next Generation Information Access, Harrods Creek, KY: Arnold Information Technology, 2015.
I have known Winn since about 1992 when I first tried to force feed the US Government the concept of OSINT (“dont' send a spy where a schoolboy can go”), only to be shut down by the CIA and marginalized for 30 years because my ideas — like Winn's ideas — are threatening to the established mandarins who have gotten away with being ignorant and incompetent for decades. It is a comfort to me that time-based security has been refused for all these years just as OSINT has been refused, just as Bill Binney's Thin Thread architecture for meta data pattern analysis has been refused by NSA, and it is most exciting to me that at this point in time multiple minds are converging to create Web 3.0: Binney, Schwartau, Steele, Stallman, and one of the most able crypto pioneers whose name I cannot share at this time. Below is the short version of what I want to build, ideally in support of President Donald Trump using the Open Source Agency (OSA) as home base.
- protected valuations (coin, savings, deeds, trust, etc)
- protected tools (cannot be programmed to lie)
- protected data (cannot be erased or manipulated)
- protected communities (competition of ideas, no one can be censored)
Additional references relevant to the post-Western economy and Internet that must certainly integrate time-based security (while eliminating Amazon, Facebook, Google, MeetUp, Microsoft, Twitter, and YouTube, among others) can be viewed on the landing page for https://robertdavidsteele.com and across my many publications. WInn has delivered a manifesto that should hit every government and every corporation and every insurance company, like a solar storm. Pay attention or be fried.
See Especially:
Review: WORM – The First Digital World War
See Also:
Review: INFORMATION WARFARE–Chaos on the Electronic Superhighway




