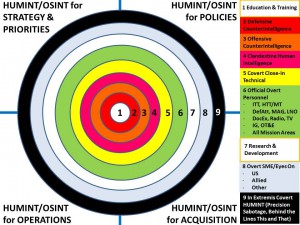
ROBERT STEELE: I have elected to answer this personally. It may well be the most fundamental question this web site has received in that any corruption in the answer to this question assures the failure of any strategy, policy, acquisition, or operation that is spawned from an inherently corrupt — a deliberately corrupt — refusal to take the question seriously.
There are several ways to address this. The first is the most obvious, which is to say that the traditional threat is state on state conventional forces, and the non-traditional threats are everything else. Here in one chart is what General Al Gray, USMC, then Commandant of the Marine Corps, with my assistance as his ghost-writer, put in “Global Intelligence Challenges in the 1990's” (American Intelligence Journal, Winter 1989-1990).
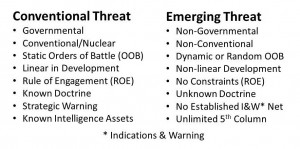
The whole point of that article was to suggest that both the US Intelligence Community and the US Department of Defense needed to radically alter how they trained, equipped, and organized. I now realize that it was corruption, not stupidity, that buried this message. As SOCOM and Navy Irregular Warfare said in defending their decision not to go after the Somali pirates from 2005-2008 and later, “it's not an expensive enough problem.”
Continue reading “2013 Robert Steele Reflections on [Search:] non+traditional+threat 1.2”