
Why Criminal Hackers Must Not Be Rewarded
Part 1: The Fruit of the Poisoned Tree
By M. E. Kabay, 11/30/2009
In 1995, I participated in a debate with distinguished security expert Robert D. Steele, a vigorous proponent of open-source intelligence. We discussed the advisability of hiring criminal hackers. Perhaps readers will find the polemic I published back then of interest today. I’m sure it will provoke vitriolic comments from the criminal hacker community.
Phi Beta Iota: Mich Kabay was then and is now one of the very best digital security professionals, and our admiration for him is unbounded. Below is the slide he provided for our use in the keynote address to the National Security Agency (NSA) in Las Vegas. Mich has always had difficulty distinguishing between hackers and criminals–just as today corporations are firing digital natives that route around their really dumb security systems so they can multi-task by leveraging their home computer, governments are making the mistake of budgeting billions of dollars for “cyber'swecurity” where no amount of money will make up for basic idiocy at the management level, AND there are not enough cyber-wizards to go around. Mitch's slide from the late 1990's remains valid: we do more damage to ourselves because of bad management and ignorant management than any criminal hacker might do. We also waste precious resources that could be applied to creating a Smart Nation. Had the US Government paid attention when we introduced them to hackers in 1993-1994 as a vital national resource, we would today have a cyber-corps of gifted folk who would by now have locked down what really matters, and opened up external assets of vital interest to the Republic. We have wasted over fifteen years.
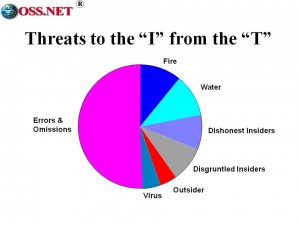
Mich E. Kabay, The NCSA Guide to Enterprise Security: Protecting Information Assets, McGraw-Hill (New York, 1996). ISBN 0-07-033147-2. Chapter 1, Figure 1, page 11. The figure in the book is superseded by this table, provided by Dr. Kabay in personal communications to Robert Steele, OSS CEO, 12 March 1998.
Journal: Cyber-Idiocy Two, Cyber-Sense Zero
Journal: Cyber-Security or Cyber-Scam? Plus Short List of Links to Reviews and Books on Hacking 101
Search: InfoOps (Information Operations (IO))



