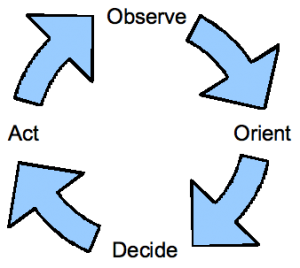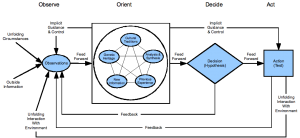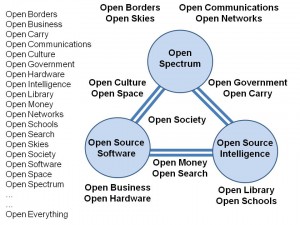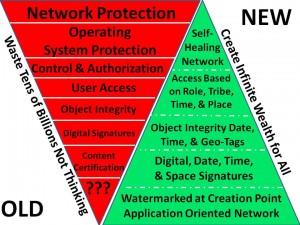
Old Information Operations (IO) is too focused on the “Maginot Line” of legacy technology badly integrated and poorly understood. New Information Operations (IO) is the “Maneuver Warfare” of the Information Age. The integrity is in the user and data, not the system. Truth & trust rather than deception & jamming are the primordal enablers.
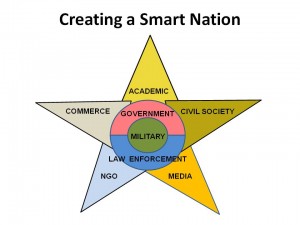
This is an improvisation working off Robert Garigue's slide, “Control Framework is a hierarchy of accountability structures”from his briefing,Robert Garigue: The New Information Security Agenda–Managing the Emerging Semantic Risks and Robert Steele's slide, Epoch B Leadership. It is NOT POSSIBLE to “command” cyber-security from the “top down.” One can only build in accountability and resiliency–which is to say, intelligence and integrity–from the bottom up. Education, not technology, is the core change agent. Human-centered design driven by intelligence is the architect, NOT pseudo-engineering from contractors seeking profit at any cost.
See Also: