Terrorist Attack Map Shows Terrorism ‘Hot Spots' Across U.S.
Can science predict where terrorists will strike? Not quite. But researchers at the University of Maryland (UMD) and the University of Massachusetts, Boston (UMB) have created a detailed map of where terrorism attacks have occurred since 1970 – and it reveals some big surprises.
The map's accompanying study, conducted at the UMD's National Consortium for the Study of Terrorism and Responses to Terrorism (START), found that while certain areas (those surrounding Manhattan and Los Angeles, for example) have endured as terror ‘hot spots' throughout the study, others have come and go. In the 2000s, for example, there has been a higher-than-average rate of attacks in Maricopa County, AZ, Phoenix's county. King County, WA, on the other hand, was a terror hot spot in the 1970s and 1980s, but has been largely quiet since.
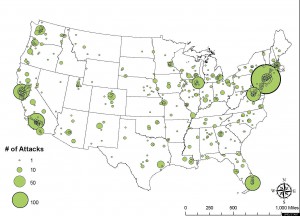
The START researchers called 65 of the nation's 3,143 counties hot spots, although that only means that these counties experienced higher than the national average of 6 attacks from 1970-2008.
The study, which looked at all 3,143 U.S. counties, also found that terrorism hot spots and motivations have changed dramatically from decade to decade. Where do terrorists come from? In the last decade, many politicians have conjured the image of Islamic fundamentalists from the Middle East. But in the 1970s, many attacks classified as ‘terrorist' came from left-wing groups in Berkeley, San Francisco and surrounding areas.
The research showed a strong association between the county in which a terrorist attack occurred and its motivation. “For example,” a University of Maryland statement notes, “Lubbock County, Texas, only experienced extreme right-wing terrorism while the Bronx, New York, only experienced extreme left-wing terrorism.”
Similarly, particular ideologies' inclination to terrorist attacks varied over the years.
“The 1970s were dominated by extreme left-wing terrorist attacks,” co-author Bianca Bersani, assistant professor of sociology at UMB, said. “Far left-wing terrorism in the U.S. is almost entirely limited to the 1970s with few events in the 1980s and virtually no events after that.” Perhaps unsurprisingly, domestic left-wing terrorism overwhelmingly took place in the San Francisco Bay area during the Vietnam War.
Other interesting findings include the fact that “religiously motivated attacks occurred predominantly in the 1980s, extreme right-wing terrorism was concentrated in the 1990s and single issue attacks [‘e.g., anti-abortion, anti-Catholic, anti-nuclear, anti-Castro'] were dispersed across the 1980s, 1990s and 2000s.”
The researchers hope that the insights from the study can be used to determine the relationship between terrorism and ordinary crime, which has historically been much easier to predict.