This handbook was created to address the principle challenge for good governance — waste — and the stink that accompanies waste. The solutions in this handbook will, in our view, scale.
Jean Lievens: The Do It Yourself Maker Movement
Hardware, Manufacturing, Materials, Resilience, Software, Transparency
“In this chapter, we investigate the maker subculture and its manifestation in fabbing ecosystem. In other words, how the love of making things, hacking, tinkering, circuit bending and doing/making everything so-called DIY is a significant peculiarity of Fab Labs. We first look at the meaning and the emergence of the maker subculture and the development of hackerspaces and shared machines shops. Secondly, we explore how the maker community is shaped and organized. In a third point, this chapter details a Fab approach of architecture, art and fashion. Finally, we see how hobbyists moved from do-it-yourself (DIY) to do-it-together (DIT) activities with examples of making music instruments and biotech.”
Complete P2P Foundation Page below the line. Links added.
Continue reading “Jean Lievens: The Do It Yourself Maker Movement”
Berto Jongman: Security for the Internet of Things — Cars Can Be Hijacked and Used to Murder People — This Matters
SoftwareRethinking Security for the Internet of Things
by Chris Clearfield
Harvard Business Review, June 26, 2013
Cyber attacks, once primarily directed against networks to steal confidential information and wreak virtual havoc, have begun to expand and are now directly affecting the physical world. For example, the recent hacking of the Associated Press's Twitter account by the Syrian Electronic Army and subsequent tweet about an explosion at the White House caused the U.S. stock market to decline almost 1% before the news was revealed as a hoax. In 2010 the computer worm Stuxnet was discovered and implicated in the attack that caused physical damage to centrifuges at Iranian nuclear enrichment facilities. In 2012 a hacker built and revealed a simple device that can open Onity-brand electronic locks (which secure over 4 million hotel room doors) without a key.
The growing Internet of Things — the connection of physical devices to the internet — will rapidly expand the number of connected devices integrated into our everyday lives. From connected cars, iPhone-controlled locks (versions of which here, here, and here are in or close to production), to the hypothetical “smart fridge” that will one day order milk for me when I've run out, these technologies bring with them the promise of energy efficiency, convenience, and flexibility. They also have the potential to allow cyber attackers into the physical world in which we live as they seize on security holes in these new systems.
Mini-Me: John Pilger Interviews Julian Assange on Tactics, Techniques, and Procedures for Protecting Liberated Information Across All Boundaries
Crowd-Sourcing, Design, Innovation, Politics, Software, Transparency
Huh?
Julian Assange In Conversation With John Pilger
An extended interview with Julian Assange recorded during filming of John Pilger’s latest film The War You Don’t See.
The attacks on WikiLeaks and its founder, Julian Assange, are a response to an information revolution that threatens old power orders, in politics and journalism.
The incitement to murder trumpeted by public figures in the United States, together with attempts by the Obama administration to corrupt the law and send Assange to a hell hole prison for the rest of his life, are the reactions of a rapacious system exposed as never before.
The US Justice Department has established a secret grand jury just across the river from Washington in the eastern district of the state of Virginia. The object is to indict Julian Assange under a discredited espionage act used to arrest peace activists during the first world war, or one of the war on terror conspiracy statutes that have degraded American justice.
Judicial experts describe the jury as a deliberate set up, pointing out that this corner of Virginia is home to the employees and families of the Pentagon, CIA, Department of Homeland Security and other pillars of American power.
Phi Beta Iota: From a professional intelligence point of view, the two take-aways are 01) that insider sources for WikiLeaks are proliferating, and 02) such sources are virtually guaranteed total anonymnity for their one-time or limited “donations.” US military now serving or having recently served in Afghanistan and Iraq appear to be the predominant source group.
Patrick Meier: Using Waze, Uber, AirBnB and SeeClickFix for Disaster Response
Crowd-Sourcing, Design, Geospatial, Governance, Software
Using Waze, Uber, AirBnB and SeeClickFix for Disaster Response
After the Category 5 Tornado in Oklahoma, map editors at Waze used the service to route drivers around the damage. While Uber increased their car service fares during Hurricane Sandy, they could have modified their App to encourage the shared use of Uber cars to fill unused seats. This would have taken some work, but AirBnB did modify their platform overnight to let over 1,400 kindhearted New Yorkers offer free housing to victims of the hurricane. SeeClick fix was used also to report over 800 issues in just 24 hours after Sandy made landfall. These included reports on the precise location of power outages, flooding, downed trees, downed electric lines, and other storm damage. Following the Boston Marathon Bombing, SeeClick fix was used to quickly find emergency housing for those affected by the tragedy.
Read full post with additional graphics and links.
Continue reading “Patrick Meier: Using Waze, Uber, AirBnB and SeeClickFix for Disaster Response”
Patrick Meier: Analysis of Multimedia Shared on Twitter After Tornado — Instagram Rules
Crowd-Sourcing, Geospatial, P2P / Panarchy, Resilience, Software, Transparency
Analysis of Multimedia Shared on Twitter After Tornado
Humanitarian organizations and emergency management offices are increasingly interested in capturing multimedia content shared on social media during crises. Last year, the UN Office for the Coordination of Humanitarian Affairs (OCHA) activated the Digital Humanitarian Network (DHN) to identify and geotag pictures and videos shared on Twitter that captured the damage caused by Typhoon Pablo, for example. So I’ve been collaborating closely with my colleague Hemant Purohit to analyze the multimedia content shared by millions of tweets posted after the Category 5 Tornado devastated the city of Moore, Oklahoma on May 20th. The results are shared below along with details of a project I am spearheading at QCRI to provide disaster responders with relevant multimedia content in real time during future disasters.
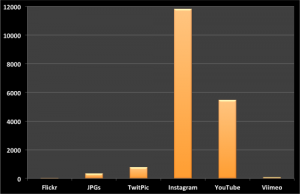
For this preliminary multimedia analysis, we focused on the first 48 hours after the Tornado and specifically on the following multimedia sources/types: Twitpic, Instagram, Flickr, JPGs, YouTube and Vimeo. JPGs refers to URLs shared on Twitter that include “.jpg”. Only ~1% of tweets posted during the 2-day period included URLs to multimedia content. We filtered out duplicate URLs to produce the following unique counts depicted above and listed below.
- Twitpic = 784
- Instagram = 11,822
- Flickr = 33
- JPGs = 347
- YouTube = 5,474
- Vimeo = 88
Clearly, Instagram and Youtube are important sources of multimedia content during disasters. The graphs below (click to enlarge) depict the frequency of individual multimedia types by hour during the first 48 hours after the Tornado. Note that we were only able to collect about 2 million tweets during this period using the Twitter Streaming API but expect that millions more were posted, which is why access to the Twitter Firehose is important and why I’m a strong advocate of Big Data Philanthropy for Humanitarian Response.
Robin Good: Automated Topic-Specific Online Curation Tool
Crowd-Sourcing, Culture, Design, Innovation, Knowledge, P2P / Panarchy, Software Kurator is a web service which allows you to easily customize one or more visual magazines that automatically aggregate the hashtags, lists, Twitter users, Facebook pages and RSS feeds you specify.
Kurator is a web service which allows you to easily customize one or more visual magazines that automatically aggregate the hashtags, lists, Twitter users, Facebook pages and RSS feeds you specify.
Specifically, you can aggregate from the following sources:
- Twitter User
- Twitter List
- Twitter Keywords
- Twitter Hastags
- Twitter Mentions
- Twitter Top Followers
- Facebook Page
- Facebook Keywords
- RSS Feed
You can also filter and specify specific keywords that you want to be included/excluded.
Kurators offers the ability to title each stream, and to customize somewhat the look of the final magazine by providing a few templates and layouts and access to the controls to adjust the font style, size and color.
The final stream can be published as a web page on Kurator or exported directly to WordPress as a “page”.
Continue reading “Robin Good: Automated Topic-Specific Online Curation Tool”

