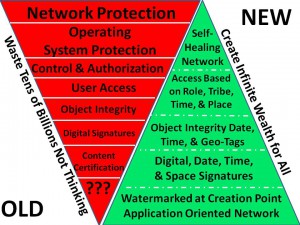
When in doubt create another layer.
Keystroke Crackdown, page 1 of 2, Army Times 07May12
Keystroke Crackdown, page 2 of 2, Army Times 07May12
Phi Beta Iota: First off, keystroke monitoring and download monitoring are already fully developed (as well as remote virtual screen replication). If Army really thinks they are investing in something new, this is a terrible indicator of how little Army knows. The idea that some contractor out there can be paid to feed “fake data” to a real-time possible suspect, is a foundation for expensive fraud. Army continues to do the wrong thing righter, while completely avoiding the right thing: human education and system design from the bottom up.
See Also:
Who’s Who in Cyber-Intelligence: Robert Garigue