Graphic: Nuclear Incidents Since 1952
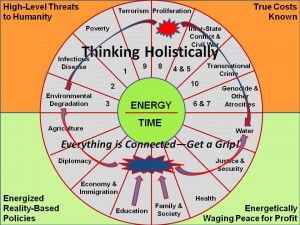
Balance, Corruption, Multinational Plus, Strategy-Holistic Coherence, Threats, True Cost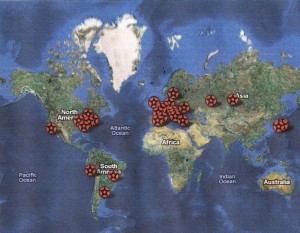
Nuclear power plant accidents: listed and ranked since 1952 guardian.co.uk Datablog: “We have identified 33 serious incidents and accidents at nuclear power stations since the first recorded one in 1952 at Chalk River in Ontario, Canada. The information is partially from the International Atomic Energy Authority – which, astonishingly, fails to keep a complete historical database – and partially from reports. Of those we have identified, six happened in the US and five in Japan. The UK and Russia have had three apiece. Using Google Fusion tables, we've put these on a map, so you can see how they're spread around the globe…” Complete reference article
Robert Garigue & Robert Steele: From Old IO to New IO
Advanced Cyber/IO, Analysis, Balance, Capabilities-Force Structure, Citizen-Centered, Collection, Earth Orientation, Geospatial, ICT-IT, Innovation, Languages-Translation, Leadership-Integrity, Multinational Plus, Policies-Harmonization, Processing, Reform, Strategy-Holistic Coherence, Threats, Tribes, True Cost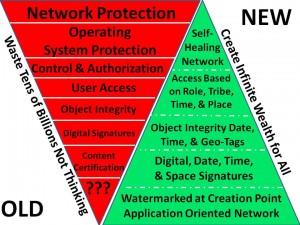
Old Information Operations (IO) is too focused on the “Maginot Line” of legacy technology badly integrated and poorly understood. New Information Operations (IO) is the “Maneuver Warfare” of the Information Age. The integrity is in the user and data, not the system. Truth & trust rather than deception & jamming are the primordal enablers.
This is an improvisation working off Robert Garigue's slide, “Control Framework is a hierarchy of accountability structures”from his briefing,Robert Garigue: The New Information Security Agenda–Managing the Emerging Semantic Risks and Robert Steele's slide, Epoch B Leadership. It is NOT POSSIBLE to “command” cyber-security from the “top down.” One can only build in accountability and resiliency–which is to say, intelligence and integrity–from the bottom up. Education, not technology, is the core change agent. Human-centered design driven by intelligence is the architect, NOT pseudo-engineering from contractors seeking profit at any cost.
See Also:
Robert Garigue: The New Information Security Agenda–Managing the Emerging Semantic Risks
Advanced Cyber/IO, Historic Contributions, ICT-IT, Innovation, Strategy-Holistic Coherence, ThreatsRobert Garigue: Feedback for Dynamic System Change
Advanced Cyber/IO, Analysis, Balance, Citizen-Centered, ICT-IT, Innovation, Leadership-Integrity, Multinational Plus, Policies-Harmonization, Processing, Reform, Strategy-Holistic Coherence, Threats, Tribes, True Cost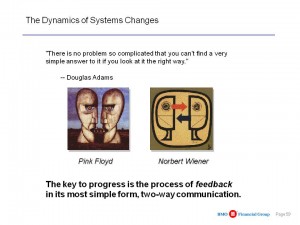
Information security is not a static process–you cannot “lock down” information the way the Air Force has tried to do, prohibiting all flash drives because it has failed over decades to actually embed security in every aspect of the process from human to download alerts. Interactive feedback loops are simple and effective. Winn Schwartau pioneered time-based security and risk-based security. Now if we just accept the fact that 80% or more of the information we need to be effective is not secret, not in English, and often not online at all, this represents a 180 degree turn away from the current focus on centralized cyber-security to the exclusion of all else (such as mission effectiveness). As Russell Ackoff put forward: we have been doing the wrong thing righter, and are about to spend $12 billion doing the wrong thing righter, instead of going ALL STOP and redesigning all systems, human to technical, around M4IS2 (multinational, multiagency, multidisciplinary, multidomain information-sharing and sense-making). One can no more merge all the Serious Games into one World Game than one can merge all the stovepipes into one “all-source” system. We have to do a clean-sheet requirements review and design for M4IS2 success, otherwise we automatically default to more of the failures that NSA and its various contractors are so notorious for….
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
Robert Garigue: Role of the Chief Information Security Officer
Advanced Cyber/IO, Balance, ICT-IT, Innovation, Leadership-Integrity, Multinational Plus, Policies-Harmonization, Reform, Strategy-Holistic Coherence, Threats, True Cost
IMPORTANT: The Chief Information Security Officer (CISO) is not the Chief Knowledge Officer (CKO) nor the Mission Commander or the Mission Logistics Officer or any of the other mission support specialties. The point is that security and knowledge must co-exist and in collaboration with one another, the CISO and CKO need to ensure that the force is trained, equipped, and organized so that the right information is available to the right person at the right time in the right format. If in doubt, err on the side of access, not control. It is much easier to do that if you are honest about NOT classifying the 80% that should NOT be classified.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing
Robert Garigue: Three Information Security Domains–the Physical (Old), the Process (Current), and the Content (Future)
Advanced Cyber/IO, Citizen-Centered, ICT-IT, Policies-Harmonization, Strategy-Holistic Coherence, Threats, True Cost
Core Point: The US national security world is still operating under a two conflicting paradigms: stovepipes within which authorized users have access to everything in the stovepipe (more or less); and isolated stovepipes in which external authorized users have to spend 25% of their time gaining access to 80+ databases (or worse, don't bother), and if they forget their password, a 2-3 day gap while access is restored. What SHOULD have happened between 1986 when this was first pointed out and 1994 when the national alarm was sounded, was full excryption at rest of all documents, and a combination of automated access roles and rules together with anomaly detection at any point in the system including external drives. The good news: 90% or more of what needs to be shared is NOT SECRET. Bad news: someone other than the US Government “owns” that 90%. The US system is not capable of ingesting and then exploiting that 90%.
See Also:
Robert Garigue, “Technical Preface” to Book Three
Robert Garigue, CISO Briefing


