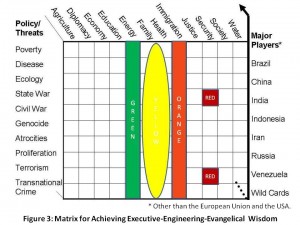
Phi Beta Iota: This started as a short list for the various college and university engineering students that have dialed in, but as we got into it, it became more of a “situational awareness” inventory pulling together both technical “solutions” none of which have been integrated yet, and analytic “requirements” none of which have been satisfied yet.
$75 billion a year for secret intelligence, and we still do not have an analytic desktop toolkit, all-source geospatially and historically and cultural astute back office processing, or global reach to all humans, all minds, all the time. Sucks for us. Let's see what the Smart Mob can do….
We specifically invite suggestions in the Comments for removing items from this list, or for adding items from within this website or from any other website. This is now a work zone. Steele is available to visit any engineering workshop and especially those working on bottom-up clouds like Swarm DPL (transparently scalable distributed programming language).
See also About the Idea, Articles, Briefs, Handbooks, and Historic Contributions. Use the Menu–everything on this stie responds to “OSINT” that is not a good search term. Rock on!
TOTALLY TECH:
2009 Arnold Google: The Digital Gutenberg
2008 Memoranda: Policy-Budget Outreach Tool