SchwartzReport: How Big Finance Has Killed US Economy Including Innovation
03 Economy, Commerce, Commercial Intelligence, Corruption, IneptitudeThis is a really good take on what is happening financially, and why it has a deadening effect on technological development. When immediate profit is your only priority, there are no correcting forces, and you slowly go off course in terms of wellness. Until you crash. We ask the wrong questions so we get the wrong answers. Author’s note: This post is based on papers presented and remarks made during a *conference panel I moderated featuring William Lazonick of U Mass-Lowell, Jan Kregel of the Levy Institute and Damon Silvers of the AFL-CIO.
Big Finance Is Strangling Innovation
LYNN STUART PARRAMORE, Senior Editor – Salon/AlterNet (U.S.)
Chuck Spinney: Sick People at Aspin Summit II
07 Other Atrocities, Commerce, Corruption, Government, Idiocy
FYI … some of this attached NYT report seems to have been sourced in part on the “meeting at the Aspen Inst., reported by Max Blumenthal in Alternet (See “Shocking ‘Extermination' Fantasies By the People Running America's Empire on Full Display at Aspen Summit”), which I distributed earlier this week.
Note how the information in this NYT report is consistent with a need for even greater surveillance of John Q Average American. This helps to prop up the establishment’s panicky pushback against the growing populist threat to rein in NSA’s snooping that became so evident in the surprisingly narrow defeat of the Amash Amendment — a panic which Blumenthal noted was also on display in the Snowden angst pervading Aspen.
Now think of the unstated elegance implicit in the closed loop of the snooping mentality on display in these two reports: The US and its European establishments (and the Sunni Gulf Monarchies) stoke up a sectarian revolt against Syrian President Assad. Predictably, the best fighters in the revolt are radical Sunni Jihadis, many of whom were trained by our wars in Iraq and Libya and perhaps Afghanistan. Also predictably, given Jihadi spillover from Libya, the radical Jihadis take over the Syrian revolt. The US and Europeans now claim these Syrian Jihadis are attracting Jihadi wannabees from the West (also predictable), who may return to the Europe and US, where they can use their enhanced terrorist skills and Al Qaida connections to wreak havoc at home. Therefore, given the new domestic threat created by the Establishment's policies of perpetual war, we need to increase NSA surveillance (really data mining) capabilities to sniff out indicators of prospective terrorist behaviour at home. Naturally, to do this, we must accept the greatly increased risks of false positives* implicit in all data mining schemes, because they all rely on the mechanistic assumption that the targets of the mining action will not bother to modify their behaviour sufficiently to neutralize their identification by the data mining algorithm or template. (A rather peculiar assumption given the proactive conspiratorial confrontation dynamics so pervasive throughout the Middle East.)
Of course, these legal niceties of avoiding false positives are irrelevant, because thanks to the Patriot (Enabling?) Act, we can detain targets without charging them, and besides, the real threats to be neutralized are the outliers at home who are trying to defend and anachronistic Fourth Amendment like Congressmen Amash and Conyers. So, a few more false positives of innocent John Q. Average Americans are merely collateral damage that must be accepted in the defense of ‘freedom' in the perpetual wars of American Empire.
—————————–
* A false positive occurs when a statistical deduction tells you something is true when it is in reality not true. Finding an innocent man guilty of a crime is a false positive, and it is no accident that most legal systems in democracies are premised, at least in theory, on a value system that it is more important to avoid false positives and than false negatives (i.e. it is more important not to convict and innocent person than to fail to convict a guilty person)
Worries Mount as Syria Lures West’s Muslims
By ERIC SCHMITT
The New York Times, July 27, 2013
WASHINGTON — A rising number of radicalized young Muslims with Western passports are traveling to Syria to fight with the rebels against the government of Bashar al-Assad, raising fears among American and European intelligence officials of a new terrorist threat when the fighters return home.
Continue reading “Chuck Spinney: Sick People at Aspin Summit II”
Stephen E. Arnold: Search Hits the “Big O” – Robert Steele Comments on IT’s Three Sucking Chest Wounds
Advanced Cyber/IO, IO Impotency
Big O Explained: Why Systems Are Alike?
Posted: 27 Jul 2013 04:30 AM PDT
In several of my recent lectures, I pointed out that most end users cannot differentiate among search systems. The comment made about these systems is often, “Why can’t these systems be like Google?” I concluded that the similarity of requests suggests that systems are essentially identical.
One reason is that training in university and the “use what works” approach in the real world produces search, content processing, and analytics systems that are pretty much indistinguishable. There are differences, but these can be appreciated only when a person takes the systems apart. Even then, differences are difficult to explain; for example, why a threshold value in System A is 15 percent lower than in System B. When dealing with sketchy data, the difference is usually irrelevant.
Another reason is that today’s systems are struggling to cope with operations that stretch the capabilities of even the most robust systems. Developers have to balance what the engineering plan wants to do with what can be done in a reasonable amount of time on an existing system.
Enter Big O.
You may want to take a look at “Big O Notation Explained by a Self-Taught Programmer.” I found the write up interesting and clear. The main point in my opinion is:
Consider this function:
def all_combinations(the_list): results = [] for item in the_list: for inner_item in the_list: results.append((item, inner_item)) return resultsThis matches every item in the list with every other item in the list. If we gave it an array
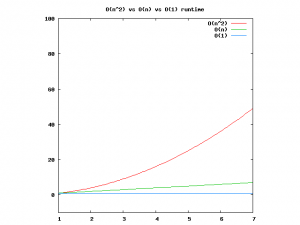
[1,2,3], we’d get back[(1,1) (1,2), (1,3), (2, 1), (2, 2), (2, 3), (3, 1), (3, 2), (3, 3)]. This is part of the field of combinatorics(warning: scary math terms!), which is the mathematical field which studies combinations of things. This function (or algorithm, if you want to sound fancy) is consideredO(n^2). This is because for every item in the list (akanfor the input size), we have to donmore operations. Son * n == n^2.Below is a comparison of each of these graphs, for reference. You can see that an
O(n^2)function will get slow very quickly where as something that operates in constant time will be much better.
Net net: Developers have to do what works. Search and related content processes are complex. In order to get the work done, search systems have embraced “what works.” Over time, we get undifferentiable systems.
Disagree? Use the comments section to explain.
Stephen E Arnold, July 27, 2013
Sponsored by Xenky

ROBERT STEELE: Information Technology (IT) has three sucking chest wounds that will persist into the foreseeable future.
1. Free energy and unlimited clean desalinated water have not been a priority for the information era nation-state and corporations. Big mistake. NSA is the poster child for poor leadership in this regard, putting a massive computing center in Utah that has neither renewable energy nor any concept of what it means to need 1.7 million gallons a day from aquifers that are so low the entire state of Utah is on water restriction for front lawns.

2. IT continues to ignore the human factor — as Jim Bamford so famously concludes one of his books on NSA, the human brain is vastly more powerful than any computer NSA might build for 20 years into the future — and as Crisis Mapping and humanitarian technologies are showing, harnessing the distributed intelligence of any given diaspora changes everything about what and when and how one can know — stuff CIA will never master under its current paradigm.

3. IT continues to ignore the demonstrated limitations of proprietary software badly coded and undocumented, generally far from standardization. Proprietary is unaffordable, is not inter-operable, and does not scale. Until we made the turn to Open Source Everything (OSE), IT will continue to return — as Paul Strassmann has documented so ably — a NEGATIVE return on investment. More money for IT in its present configuration “makes bad management worse.”
See Also:
1995 GIQ 13/2 Creating a Smart Nation: Strategy, Policy, Intelligence, and Information
2002 The New Craft of Intelligence–What Should the T Be Doing to the I in IT?
Marcus Aurelius: Al Qaeda is Back! and The Future of Al Qaeda — Shared Bottom Line? Everything the USG Does Enhances Al Qaeda Appeal!
01 Poverty, 04 Inter-State Conflict, 05 Civil War, 06 Genocide, 07 Other Atrocities, 09 Terrorism, IO Deeds of War, Lessons, Officers Call
Al Qaeda Is Back
Jailbreaks in Iraq. A surge in Syria. A growing presence in Lebanon. The terrorist group’s influence is on the rise, says Bruce Riedel.
TheDailyBeast.com, July 26, 2013
Two spectacular al Qaeda prison breaks in Iraq, freeing over 500 of its members in two separate prisons simultaneously this week, demonstrate the group is back with a vengeance. Al Qaeda’s Iraq branch is also the moving force behind the jihadist success in Syria. The resurgence of al Qaeda in Iraq has sobering implications for what is likely to follow the drawdown of NATO forces in Afghanistan for the al Qaeda mother ship in Pakistan.
The Future of Al Qaeda
PDF (88 Pages): 2013-07-28 Future of Al Qaeda
EXTRACT:
Th e speed of change throughout the Middle East and North Africa since 2011 has demonstrated that a policy of Soviet-era containment manifested since the Cold War by support for repressive dictatorships that suppressed, rather than emancipated their populations, catalysed the appeal of Al-Qaeda. Instead, as the Arab Spring has shown, populations desire economic growth, employment and good governance in the place of the defi cient development outcomes, conflict and militancy that characterise life in so much of this region. As the recently released US National Strategy for Counterterrorism elucidates, a comprehensive approach to tackling Al-Qaeda must include “objectives such as promoting responsive governance and respect for the rights of citizens, which will reduce Al-Qaeda’s resonance and relevancy.”149
SchwartzReport: Bad Bees, Ugly Death of Full-Time Jobs, Worse Who We At War With? Classified! End of America: Federal Order for Password Files
Commerce, Corruption, Government, Idiocy, Law EnforcementBAD:
Here is the latest on the plight of the bees. The headline says it all.
Scientists Discover What’s Killing the Bees and It’s Worse Than You Thought
TODD WOODY – Quartz
UGLY:
The income of the average American family is nine per cent lower than it was a decade ago, and it gets harder and harder to get a job. And now this survey showing that young adults, even when they have some work, are working full-time jobs less and less.
| In U.S., Fewer Young Adults Holding Full-Time Jobs in 2013 |
| DENNIS JACOBE, Chief Economist – The Gallup Organization |
WORSE:
We have reached the Orwellian state of continuous war. Who are we fighting? That's a secret. You are required to pay for it, but you are not entitled to know.
Who Are We at War With? That’s Classified
CORA CURRIER – ProPublica
END OF AMERICA:
Here is the latest on the American police state. If you think anything you do is private you live in a fantasy.
Feds Tell Web Firms to Turn Over User Account Passwords
DECLAN MCCULLAGH, Chief Political Correspondent – C|NET
Gordon Duff: Israeli Covert Action in USA Led by Senator John McCain?
Corruption, Government, IO Deeds of War, Military
Israeli hoax on Gen. Dempsey unmasked
Hoax exposed: Gen. Dempsey rebuffs speculations he called for Syria raids
“In truth, the calls for ‘kinetic strikes’ on Syria came from Senator John McCain of Arizona, a member of the Israeli lobby who met with Al Qaeda leaders in the Arab country in late May, 2013.”
Continue reading “Gordon Duff: Israeli Covert Action in USA Led by Senator John McCain?”

