Berto Jongman Recommends:
Impacts of Climate Change: A System Vulnerability Approach (2007)
Berto Jongman Recommends:
Impacts of Climate Change: A System Vulnerability Approach (2007)

Lifestyle Hackers
Jim Routh and Gary McGraw examine why twenty-somethings skateboard right past security controls, and what it means for employers (i.e. you!)
November 02, 2009
The insider threat, the bane of computer security and a topic of worried conversation among CSOs, is undergoing significant change. Over the years, the majority of insider threats have carried out attacks in order to line their pockets, punish their colleagues, spy for the enemy or wreak havoc from within. Today's insider threats may
have something much less insidious in mind—multitasking and social networking to get their jobs done.
The Elephant in the Room: A war of ideas within Islam
Backward views hold sway in much of the Muslim world. And yet there is hope.
By Rick Santorum Thu, Nov. 5, 2009
The students, one man and two women, wore Western-style clothes and spoke English with little or no accent. They disputed my description of Islam as it's practiced in the Middle East, maintaining that al-Qaeda's version of Islam in no way reflects the Islam that is practiced around the world.
So I asked them a question: Should apostates – Muslims who convert to another religion – be subject to execution?
One of the women quickly said no. She insisted that she was free to leave Islam if she wanted to, and that she knew other people who had done so without a problem – in the United States.
I said I wasn't talking about her and others' freedom of religion in this country. What if they lived in a Muslim-majority country?
Silence. Eventually, the young man blurted out, “That's different.”

Challenge features 10 red balloons
By Doug Beizer Nov 04, 2009
A contest planned by the Defense Advanced Research Projects Agency (DARPA) will challenge contestants to use the Internet to locate the 10 large red weather balloons the agency will place across the continental United States, DARPA officials announced last week. DARPA will put the balloons in publicly accessible locations and display them for one day during daylight hours. The first participant to identify the latitude and longitude of all the balloons will receive the $40,000 cash prize. The balloons will be positioned Dec. 5, DARPA officials said Oct. 29.
Phi Beta Iota: This is a no-brainer for Twitter–Graphics: Twitter as an Intelligence Tool

This interview is part of the Institute's “Conversations with History” series, and uses Internet technology to share with the public Berkeley's distinction as a global forum for ideas.
In this landmark work, the culmination of thirty years of systematic, comprehensive comparison of nineteen rich democracies, Wilensky answers two basic questions: What is distinctly modern about modern societies? In what ways are they becoming alike, and how do variations in types of political economy shape system performance? The book is being hailed as “a monumental work,” “an instant classic,” “a truly amazing accomplishment.”
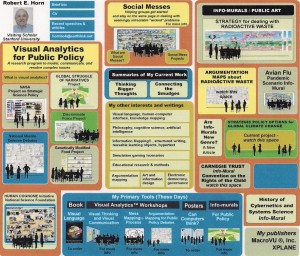
Phi Beta Iota: Our most trusted alter ego flagged this for attention, and we love it. We have ordered the book on Visual Language and hoping the author will soon publish on Information Mapping. This is sheer genius, not least for its human sensitivity and its grasp of the brain-eye-hand-touch loop. We are blown away by this, it buries the visual design phenoms of the past, while clearly being relevant to Collective Intelligence and Conscious Evolution.

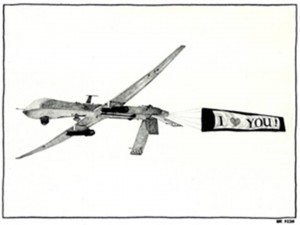
Military Refines A ‘Constant Stare Against Our Enemy'
The rapidly increasing surveillance power of unmanned aircraft gives U.S. officials an option beside s troops
By Julian E. Barnes November 2, 2009 Pg. 1
WASHINGTON — The Pentagon plans to dramatically increase the surveillance capabilities of its most advanced unmanned aircraft next year, adding so many video feeds that a drone which now stares down at a single house or vehicle could keep constant watch on nearly everything that moves within an area of 1.5 square miles.
The year after that, the capability will double to 3 square miles.
Continue reading “Journal: Constant Technical Stare vs. Engaged Brain”