Graphic: Alberts-Steele M4IS2
Advanced Cyber/IO, Capabilities-Force Structure, ICT-IT, Innovation, Leadership-Integrity, Multinational Plus, Processing, Strategy-Holistic CoherenceJournal: ClimateGate–“The Trick” Explained
03 Environmental Degradation, 05 Energy, Communities of Practice, Earth Intelligence, Earth Orientation, Ethics, Key Players, PoliticalSearch: Intelligence Community Wheel
Balance, Citizen-Centered, Languages-Translation, Multinational Plus, Reform, Searches, Strategy-Holistic Coherence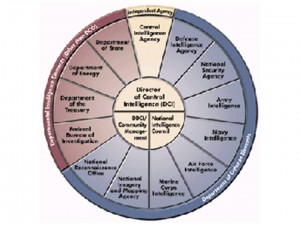
To the left is the traditional intelligence wheel, consisting of the 16 or so (there are other elements not listed) entities that in theory comprise the predominantly secret U.S. Intelligence Community.
Below is the emergent intelligence wheel that harnesses all human minds in relation to all information all the time. We still need spies and secrecy but in moderation.
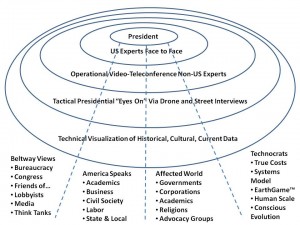
Although this version is centered on the President, it can just as easily be centered on any Cabinet Department down to the branch level, any Congressional jurisdiction, any private sector domain of interest.
See also:
Search: Seven Tribes (now Eight Tribes)
Journal: Design Thinking for Government
Review: The Design of Business–Why Design Thinking is the Next Competitive Advantage
Graphic: Multi-Lateral Sharing
Advanced Cyber/IO, Balance, Innovation, Multinational Plus, Policies-Harmonization, Processing, Strategy-Holistic Coherence, Threats, Tribes
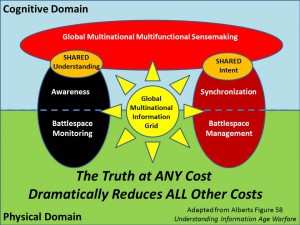
This is a 2000-2002 slide that bears on the extraordinary possibilities inherent in creating a global multinational open source information sharing and sense-making grid. The 80-20 rule really does seem to stand up under most circumstances. White Hat (Stabilization & Reconstruction, Peaceful Preventive Measures) are especially responsible to shared open source information across all boundaries.
Learn more:
2009 DoD OSINT Leadership and Staff Briefings
Search: world map with 8 conflicts
Geospatial, Leadership-Integrity, Searches, Strategy-Holistic Coherence, Threats, Tribes
o the left is the map we created when it was clear the USA was going to invade Iraq and blow what should have been the surgical demise of Osama Bin Laden. This slide was created for and used in the opening briefing to the SES course on national security at the Western Management Development Center, and in 19 briefings around the country to the American Committees on Foreign Relations (ACFR).
The only really decent conflict map, now out of production, is Berto Jongman's World Conflict & Human Rights Map also available in a Simplified World Conflict Map.
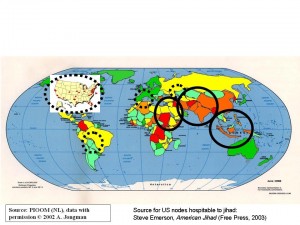
Notes: If bin Laden could have asked his maker for the most helpful possible American reaction to 9-11, he could not have done better than the Bush Administration’s ill-considered conventional military attacks on Afghanistan and Iraq. The US is now an occupying force in Iraq, and in Afghanistan it has lost control of the entire country, where under US “non-control” the opium crop has doubled, enriching all the warlords, who will be almost impossible to dislodge without resuming combat operations. We have started a six-front 100-year war.
To the right is a later version used in private briefings.
Reference: Are Hackers Pioneers with the Right Stuff or Criminal Pathological Scum? Mitch Kabay Reprises
03 Economy, 04 Education, 10 Transnational Crime, Civil Society, Collective Intelligence, Ethics, Hacking, ICT-IT, InfoOps (IO), Law Enforcement, Media Reports, Methods & Process, Mobile, Real Time, Technologies

Why Criminal Hackers Must Not Be Rewarded
Part 1: The Fruit of the Poisoned Tree
By M. E. Kabay, 11/30/2009
In 1995, I participated in a debate with distinguished security expert Robert D. Steele, a vigorous proponent of open-source intelligence. We discussed the advisability of hiring criminal hackers. Perhaps readers will find the polemic I published back then of interest today. I’m sure it will provoke vitriolic comments from the criminal hacker community.