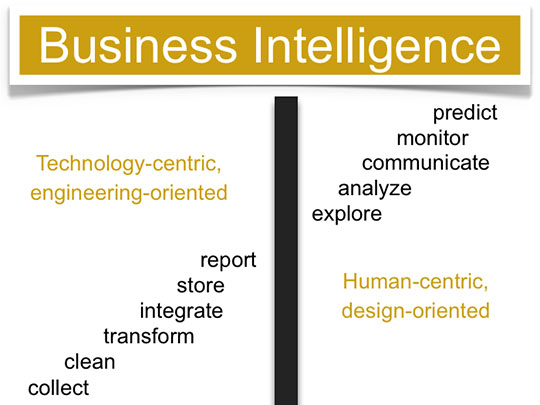
Kudos to Stephen Few, the author of this slide, whose informative web site can be reached by clicking above. As we have been saying for years, BI is data mining, nothing more. Here he shows the wall that has been separating BI from the rest of us.
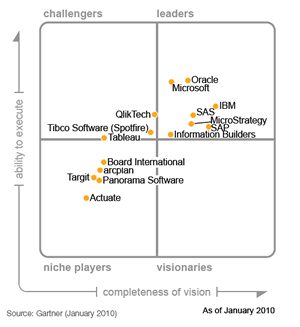
This is Gartner's latest. It comes as we are thinking about the convergence among software, hardware, and services companies, all trying to stovepipe their clients, none of them trying to help their clients actually do multinational eight-tribe information-sharing and sense-making.
Then there is the complete absence of visionaries, at least that Gartner has noticed or deigned to list.
It merits comment that “Business Intelligence” is nothing more than internal data mining, it does not integrate the other three quadrants, for that see Graphic: Four Quadrants J-2 High Cell SMS Low and Graphic: Human Intelligence (HUMINT) J-2 Central. Links to other graphics can be seen atSearch: information sharing graphic dod.
Phi Beta Iota: Most serious analysts now understand Citation Analytics 101. It's time to move to Citation Analytics 202, and there is no better way to introduce the art of the possible than by pointing to Kevin W. Boyack, Katy Borner, and Richard Klavans (2007), “Mapping the Structure and Evolution of Chemistry Research (11th International Conference of Scientometrics and Infometrics, pp. 112-123.
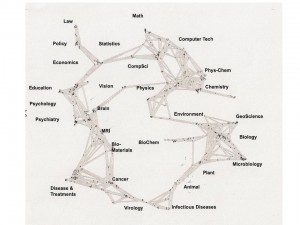

There are several take-aways from this article, which is more or less the “coming out” of the Klavens-inspired infometrics field now that he has won his law-suit and has unchallenged access to all Institute of Scientific Information (ISI) access [this was one of the sources we used to win the Burundi Exercise before the Aspin-Brown Commission in 1995].
Colombia: The Constitutional Court yesterday declared an agreement granting US military access to Colombian bases unconstitutional on procedural grounds. La Patilla reported the vote was 6-3 against the agreement, and Semana reported the court would soon give a press conference to explain the details. The constitutional court ruled the 2009 accord should be redrafted as an international treaty and sent to Colombia's Congress for approval.
The agreement would have allowed US forces to have access to seven Colombian bases that help support operations against drug trafficking and terrorism. This is the draft legislation that other Latin American leaders criticized lat year because it abetted a rise in US regional influence.
The deal agreed by former President Alvaro Uribe in October 2009 gave the US access to the bases for 10 years and would see a maximum of 800 US military personnel and 600 civilian defense contractors based in Colombia.
The court's chief justice Mauricio Gonzalez said the deal was “an arrangement which requires the State to take on new obligations as well as an extension of previous ones.” He said that as such, it should be “handled as an international treaty, that is, subject to congressional approval”. The court did not rule on the legitimacy of the agreement itself and the ruling does not mean the US has to leave the country altogether.
NIGHTWATCH Comment: President Juan Manuel Santos said the court ruling will have little impact on U.S. military help fighting rebels and will not affect the operations of U.S. troops and contractors working with Colombia's military, The Associated Press reported 18 August. The ruling is primarily procedural not substantive. Nonetheless, it will be an inconvenience.
 Phi Beta Iota: Here is a rough graphic showing the four spheres of influence that are fighting World War III. Nations are flexing their Constitutional muscles against US and external incursions, while at the same time, hybrid organizations and “hidden powers” are fighting in the shadows. Most Nation-States are no longer central because they have lost its legitimacy from a mix of internal corruption and external misadventure.
Phi Beta Iota: Here is a rough graphic showing the four spheres of influence that are fighting World War III. Nations are flexing their Constitutional muscles against US and external incursions, while at the same time, hybrid organizations and “hidden powers” are fighting in the shadows. Most Nation-States are no longer central because they have lost its legitimacy from a mix of internal corruption and external misadventure.
It is neither possible nor desireable to “fight” the established powers–Non-Zero Strategy requires a focus on the five billion and the creation of infinite wealth with social capitalism and Information Communication Technologies (ICT) as well as energy, food, and other innovations. Non-violent innovation is the only viable winning strategy.
Search: world map with 8 conflicts

Phi Beta Iota: STRONG ANGEL was the other major innovation besides CATALYST, Analysis 2000, and MCIA JNID. Below is Round II from STRONG ANGEL, with Round II from M4IS2 soon to be made public, built around SILOBREAKER (actually, Son of SILOBREAKER). We considered forcing visits to the Synergy Strike Force home page, but decided that the richness of the content there needed to be displayed here.
I. Introduction
Welcome to the MESS-KIT wiki: Minimum Essential Software Services for Knowledge and Information Transfer
II. Structure
The MESS-KIT system is composed of three basic components — the software package, the virtual environment and the hardware:
a. APPLICATION SOFTWARE PACKAGE: One or more Virtual Machine Instances that package together an operating system with a web server environment and all free-and-open-source/commercial-off-the-shelf software modules. Example: A VMware instance of an Ubuntu Linux installation with a full LAMP web server hosting environment and associated web software.
b. VIRTUAL MACHINE CLIENT SOFTWARE: One Virtual Machine Software Client to package, distribute, and host one or more Application Software Packages and abstract the application software from the host operating system. Examples: VMWare Fusion and Sun VirtualBox.
c. HARDWARE: Hardware on which the Virtual Machine Client Software and Application Software Package will run. The Hardware will include a host operating system. Examples: MacMini running OSX, ASUS eeePC Netbook running eeeBuntu Linux.
Continue reading “Handbook: Synergy Strike Force, Dr. Dr. Dave Warner, Round II”