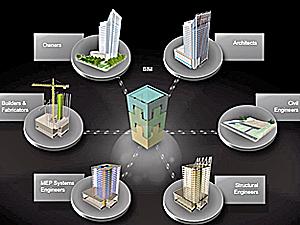
OAKLAND, CA — Building information modeling can be a valuable tool for architects, engineers and contractors that allows them to explore different design options, see what projects will look like and understand how a structure will perform long before it's built.
BIM, as it's known in the industry, also can help building owners and operators throughout a structure's lifecycle by providing visual context to performance-related data, retrofit plans and other projects intended increase energy efficiency.
In a webcast on Tuesday moderated by GreenBiz.com Executive Editor Joel Makower, representatives for design software giant Autodesk, DPR Construction and the consulting engineering firm Glumac talked about “How Building Information Modeling Solutions Transform Sustainable Design.”
– – – – – – –
Increased costs of energy, ongoing challenges posed by the economy and concerns about sustainability, market demands, occupany and eventual regulation of carbon output combine to make building owners, operators and managers increasingly aware of how their properties perform — and compare with others.
Those issues and the availability of state and federal incentives are powerful drivers to improve portfolios. “Not surprisingly, large multinational companies are getting their buildings in order,” Deodhar said.
Examples include Walmart, which will retrofit 500 buildings this year, Marriott, whose hotel chain includes 275 hotels that bear the Energy Star label, and Starbucks, which by the close of the year will begin to seek LEED certification for all new company-owned stores around the world.
Globally, buildings account for about 40 percent of energy consumption and more than 200 million buildings are candidates for efficiency improvements, Deodhar said. But optimizing a building's environmental performance requires incorporating interrelated factors, such as location, orientation, internal systems, how the building is used and other variables, into design.
Read full article (long and valuable)
Phi Beta Iota: This is the kind of project we had in mind for DIA/DO (Directorate of Open Sources & Methods). Apart from DoD being the biggest gorilla on the planet where any improvement can be measured in billions of dollars, this is the tip of the “true cost” iceberg and a success here could be immediately extended to every aspect of acquisition across all mobility, weapons, and other systems, over to the rest of the federal government, down to state and local, and out to the world. In the 21st Century design is intelligence, intelligence is design, and intelligent design, not weapons, is the influencer most likely to achieve the desired outcome.