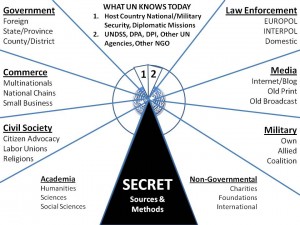
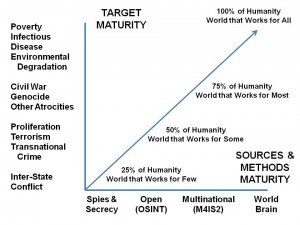
The search term brings up appropriate results, but the fact of the search gives us an opportunity to provide comment.
1) Nothing now being used by governments, and certainly not iBase or Palantir, both aging technologies that do not scale and have too many fat-finger handicaps, fulfills the originial requirements documents crafted in the late 1980's.
Worth a Look: 1989 All-Source Fusion Analytic Workstation–The Four Requirements Documents
2) The ONLY programs that have gotten anywhere close are COPERNICUS plus plus, and SILOBREAKER. However, both of these have been slow to recognize the urgency of integrating–fully integrating–capabilities that address each of the eighteen functionalities. Below is the list of softwares now in use by US Special Operations Command J-23 Open Source Intelligence Branch along with the STRONG ANGEL TOOZL and a couple of other things.
Memorandum: USSOCOM Software List and STRONG ANGEL TOOZL
See also:
Search: The Future of OSINT [is M4IS2-Multinational]
Worth a Look: Deep Web Multilingual Federated Search
1988-2009 OSINT-M4IS2 TECHINT Chronology
Worth a Look: Planetary Skin Data Sharing Initiative
Who’s Who in Librarian Intelligence: Arno Reuser
Who’s Who in Public Intelligence: Mats Bjore
Who’s Who in Collective Intelligence: Stephen E. Arnold
Journal: Dr. Dr. Dave Warner Shares…
Review: The Starfish and the Spider–The Unstoppable Power of Leaderless Organizations
Review: Innovation Happens Elsewhere–Open Source as Business Strategy
Journal: Google, the Cloud, Microsoft, & World Brain
Worth a Look: GeoChat (SMS Plotted on Map)
1998 Arnold (US) New Trends in Automated Intelligence Gathering Software
The global standard for multinational information-sharing and sense-making is in the process of being designed, funded, and distributed. If you think you have something relevant to that, generally only open source software will be considered, get in touch with any of the individuals above.