How Leaky is your country? : A Visualisation of Wikileaks

BEHIND THE CENSORSHIP OF OPERATION DARK HEART
By censoring Anthony Shaffer's new book “Operation Dark Heart” even though uncensored review copies are already available in the public domain, the Department of Defense has produced a genuinely unique product: a revealing snapshot of the way that the Obama Administration classifies national security information in 2010.
With both versions before them (excerpts), readers can see for themselves exactly what the Pentagon classifiers wanted to withhold, and can judge for themselves whether the secrecy they tried to impose can be justified on valid national security grounds. In the majority of instances, the results of such an inspection seem disappointing, if not very surprising, and they tend to confirm the most skeptical view of the operation of the classification system.
The most commonly repeated “redaction” in Operation Dark Heart is the author's cover name, “Christopher Stryker,” that he used while serving in Afghanistan. Probably the second most common redactions are references to the National Security Agency, its heaquarters location at Fort Meade, Maryland, the familiar abbreviation SIGINT (referring to “signals intelligence”), and offhand remarks like “Guys on phones were always great sources of intel,” which is blacked out on the bottom of page 56.
Also frequently redacted are mentions of the term TAREX or “Target Exploitation,” referring to intelligence collection gathered at a sensitive site, and all references to low-profile organizations such as the Air Force Special Activities Center and the Joint Special Operations Command, as well as to foreign intelligence partners such as New Zealand. Task Force 121 gets renamed Task Force 1099. The code name Copper Green, referring to an “enhanced” interrogation program, is deleted.
Perhaps 10% of the redacted passages do have some conceivable security sensitivity, including the identity of the CIA chief of station in Kabul, who has been renamed “Jacob Walker” in the new version, and a physical description of the location and appearance of the CIA station itself, which has been censored.
Many other redactions are extremely tenuous. The name of character actor Ned Beatty is not properly classified in any known universe, yet it has been blacked out on page 15 of the book. (It still appears intact in the Index.)
In short, the book embodies the practice of national security classification as it exists in the United States today. It does not exactly command respect.
A few selected pages from the original and the censored versions of Operation Dark Heart have been posted side-by-side for easy comparison here (pdf).
The New York Times reported on the Pentagon's dubious handling of the book in “Secrets in Plain Sight in Censored Book's Reprint” by Scott Shane, September 18.
** INSPECTORS GENERAL TO HELP OVERSEE CLASSIFICATION
** GAO GAINS A FOOTHOLD IN INTELLIGENCE OVERSIGHT
See Also:

America's Ruling Class — And the Perils of Revolution
By Angelo M. Codevilla from the July 2010 – August 2010 issue of American Spectator
EXTRACT 1: They [the bi-opoly two parties] think, look, and act as a class.
EXTRACT 2: The two classes have less in common culturally, dislike each other more, and embody ways of life more different from one another than did the 19th century's Northerners and Southerners — nearly all of whom, as Lincoln reminded them, “prayed to the same God.” By contrast, while most Americans pray to the God “who created and doth sustain us,” our ruling class prays to itself as “saviors of the planet” and improvers of humanity. Our classes' clash is over “whose country” America is, over what way of life will prevail, over who is to defer to whom about what. The gravity of such divisions points us, as it did Lincoln, to Mark's Gospel: “if a house be divided against itself, that house cannot stand.”
WASHINGTON — Defense Department officials are negotiating to buy and destroy all 10,000 copies of the first printing of an Afghan war memoir they say contains intelligence secrets, according to two people familiar with the dispute.
The publication of “Operation Dark Heart,” by Anthony A. Shaffer, a former Defense Intelligence Agency officer and a lieutenant colonel in the Army Reserve, has divided military security reviewers and highlighted the uncertainty about what information poses a genuine threat to security.
Continue reading “Journal: A Case Study in Confused Secrecy”
Open Sourcing U.S. Intelligence Needs
Open Source Closed
Before you get excited about joining “the OpenSource.gov community to get access to the latest open source reporting and analysis,” you should know . . . you can't. The OSC is open only to U.S. government employees, contractors, foreign liaisons and employees of the BBC Monitoring Service.
Tip of the Hat to Mario Profaca at Facebook.
See Also:
Phi Beta Iota: Most serious analysts now understand Citation Analytics 101. It's time to move to Citation Analytics 202, and there is no better way to introduce the art of the possible than by pointing to Kevin W. Boyack, Katy Borner, and Richard Klavans (2007), “Mapping the Structure and Evolution of Chemistry Research (11th International Conference of Scientometrics and Infometrics, pp. 112-123.
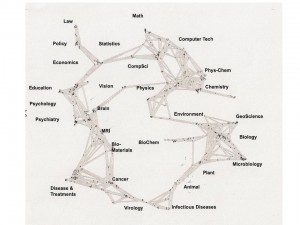

There are several take-aways from this article, which is more or less the “coming out” of the Klavens-inspired infometrics field now that he has won his law-suit and has unchallenged access to all Institute of Scientific Information (ISI) access [this was one of the sources we used to win the Burundi Exercise before the Aspin-Brown Commission in 1995].