
SEE ALSO: Journal: Gorgon Stare (All Eyes, No Brain)
The American Way of War: If You Can See Everything, Can You Know Anything?
With Air Force's new drone, ‘we can see everything,' in today's Washington Post (attached below) is a good example of how the high-cost addiction to techno war is running amok. One thing ought to be clear in Afghanistan: A tiny adversary armed with the most primitive weapons, and a command and control system made up of prayer rugs and cell phones, has brought the high tech US military to a stalemate … or even worse, the looming specter a grand-strategic defeat, because we are becoming economically and morally exhausted by the futility of this war. It does not matter whether it is President Obama presiding over a vapid strategic review or a low ranking grunt on point in Afghanistan — the central problem facing the United States in Afghanistan is the absence of what the Germans call fingerspitzengefühlor the feeling in the fingerprints needed for an intuitive feel for or connection with one's environment.
As the American strategist Colonel John Boyd (USAF Ret.) showed, fingerspitzengefühl is absolutely essential to the kind of synthetic (as opposed to analytic) thinking that is necessary for quick, relevant, and ultimately successful decision making in war, where quick decisions and sharp actions at all levels must be made and harmonized in an ever-present atmosphere of menace, uncertainty, mistrust, fear, and chaos that impedes decisive action.[1]
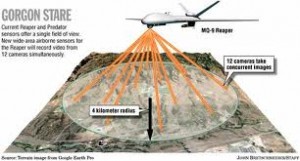
To paraphrase Clausewitz, these difficulties multiply to produce a kind of friction, and therefore, even though everything in war is simple, the simplest thing is difficult. Clausewitz considered friction is the atmosphere of war. Nevertheless, according to the Post, the Air Force is about to deploy to Afghanistan a “revolutionary airborne surveillance system called Gorgon Stare, which will be able to transmit live video images of physical movement across an entire town.”
Quoting Maj. Gen. James O. Poss, the Air Force's assistant deputy chief of staff for intelligence, surveillance and reconnaissance, “Gorgon Stare will be looking at a whole city, so there will be no way for the adversary to know what we're looking at, and we can see everything.” Nirvana. While the Post dutifully reports a smattering of opposing views, it misses the ramifications of the central idea epitomized by General Poss's confident assertion: namely, how the American ideology of techno war assumes it can negate the human need for fingerspitzengefühl on a battlefield.
General Poss's confidence suggests quite clearly he believes seeing everything enables one to know everything. This a stunning theory of knowledge. It is also a classic example of the American military's unquestioned belief that complex technologies coupled to step-by-step analytical procedures can negate the friction of combat to solve any problem in war. Lifting the fog of war is, in fact, a phrase frequently used in contractor brochures touting the efficacy of these technologies. This reflects theory of knowledge — really an unquestioned ideology — that views war as fundamentally a procedural problem of methodical analytical thinking, as opposed to its messy reality of being in large part an art of synthetic thinking.
Continue reading “Reference: Gorgon Stare–USAF Goes Nuts (Again)”




