The attached trip report documents William R. Polk's impressions of the current situation in Afghanistan based on interviews and discussions he had over a period of 10 days in August. Polk, a highly experienced American diplomat, foreign policy specialist, as well as a being a highly-regarded scholar, is the author of Violent Politics: A History of Insurgency, Terrorism, and Guerrilla War, from the American Revolution to Iraq, which is one of the very best books I have ever read on the subject of guerrilla warfare.
This very informative albeit long document covers a variety of viewpoints, each of which merits careful reading. I found the recapitulation of his discussions with Russian Ambassador Andrey Avetisyan and Mullah Abdul Salam, a former high ranking member to the Taliban, to be particularly interesting and important.
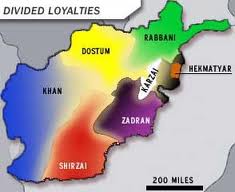
Phi Beta Iota: We read every word. Talk about deja vu. Everywhere we have ever been, the exaggeration of security and force protection, along with the absence of responsible informed strategy, leaves the Americans both out of touch with reality, and ineffective at waging peace.