
Letter to His Holiness Pope Benedict XVI
Resume Robert David STEELE Vivas M4IS2
See Also:
28 Jan Seven Answers–Robert Steele in Rome
27 Jan Assisi-Rome 2nd Meeting
27 Jan Reference: Correspondence on Assisi Intelligence

Letter to His Holiness Pope Benedict XVI
Resume Robert David STEELE Vivas M4IS2
See Also:
28 Jan Seven Answers–Robert Steele in Rome
27 Jan Assisi-Rome 2nd Meeting
27 Jan Reference: Correspondence on Assisi Intelligence

by jonl on January 10, 2011
This is something I posted in the “state of the world” conversation with Bruce Sterling on the WELL…
I give talks on the history and future of media, and on the history, evolution, and history of the Internet. I gave the talk this week to a small group gathered for lunch in a coworking space here in Austin, and after hearing the talk a technologist I know, Gray Abbott, suggested that I say more about the coming balkanization of the network as the most likely scenario. The Internet is a network of networks that depends on cooperative peering agreements – I carry your traffic and you carry mine. The high speed Internet is increasingly dependent on the networks of big providers, the telcos or cable companies like AT&T, Sprint, Verizon, Time Warner, and Comcast. They all see the substantial value supported by their networks and want to extract more of it for themselves. They talk about the high cost of bandwidth as a rationale for charging more for services – or metering services – but I think the real issue is value. When you see Google and Facebook and Netflix making bundles of money using your pipes, you want a cut. And if you’ve also tried to get into the business of providing content, it’s bothersome to see your network carrying other competing content services, including guerilla media distribution via BitTorrent.
Continue reading “Reference: Network Neutrality…Why Not…+ RECAP”

Phi Beta Iota: Notes summarizing the 59 minute video are below the line.
….Watch this!!!!! My good friend Pierre Sprey interviews Bill Hartung on Book TV about Hartung's new book, Prophets of War: Lockheed Martin and the Making of the Military-Industrial Complex.
Mr. Hartung is the director of the Arms and Security Initiative at the New America Foundation. He is the author of How Much are You Making on the War Daddy? and And Weapons for All. He's written for the Washington Post, the New York Times, the Los Angeles Times and The Nation magazine.
Summary of the 59 minute back and forth CSPAN BookTV Interview:
Continue reading “Journal: What’s Wrong with American defense….”

SEE ALSO: Journal: Gorgon Stare (All Eyes, No Brain)
The American Way of War: If You Can See Everything, Can You Know Anything?
With Air Force's new drone, ‘we can see everything,' in today's Washington Post (attached below) is a good example of how the high-cost addiction to techno war is running amok. One thing ought to be clear in Afghanistan: A tiny adversary armed with the most primitive weapons, and a command and control system made up of prayer rugs and cell phones, has brought the high tech US military to a stalemate … or even worse, the looming specter a grand-strategic defeat, because we are becoming economically and morally exhausted by the futility of this war. It does not matter whether it is President Obama presiding over a vapid strategic review or a low ranking grunt on point in Afghanistan — the central problem facing the United States in Afghanistan is the absence of what the Germans call fingerspitzengefühlor the feeling in the fingerprints needed for an intuitive feel for or connection with one's environment.
As the American strategist Colonel John Boyd (USAF Ret.) showed, fingerspitzengefühl is absolutely essential to the kind of synthetic (as opposed to analytic) thinking that is necessary for quick, relevant, and ultimately successful decision making in war, where quick decisions and sharp actions at all levels must be made and harmonized in an ever-present atmosphere of menace, uncertainty, mistrust, fear, and chaos that impedes decisive action.[1]
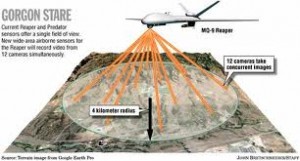
To paraphrase Clausewitz, these difficulties multiply to produce a kind of friction, and therefore, even though everything in war is simple, the simplest thing is difficult. Clausewitz considered friction is the atmosphere of war. Nevertheless, according to the Post, the Air Force is about to deploy to Afghanistan a “revolutionary airborne surveillance system called Gorgon Stare, which will be able to transmit live video images of physical movement across an entire town.”
Quoting Maj. Gen. James O. Poss, the Air Force's assistant deputy chief of staff for intelligence, surveillance and reconnaissance, “Gorgon Stare will be looking at a whole city, so there will be no way for the adversary to know what we're looking at, and we can see everything.” Nirvana. While the Post dutifully reports a smattering of opposing views, it misses the ramifications of the central idea epitomized by General Poss's confident assertion: namely, how the American ideology of techno war assumes it can negate the human need for fingerspitzengefühl on a battlefield.
General Poss's confidence suggests quite clearly he believes seeing everything enables one to know everything. This a stunning theory of knowledge. It is also a classic example of the American military's unquestioned belief that complex technologies coupled to step-by-step analytical procedures can negate the friction of combat to solve any problem in war. Lifting the fog of war is, in fact, a phrase frequently used in contractor brochures touting the efficacy of these technologies. This reflects theory of knowledge — really an unquestioned ideology — that views war as fundamentally a procedural problem of methodical analytical thinking, as opposed to its messy reality of being in large part an art of synthetic thinking.
Continue reading “Reference: Gorgon Stare–USAF Goes Nuts (Again)”
Everybody is putting out their Top 10 lists of predictions for 2011. Not to be left out of the party, below is a list of what we expect to see in 2011 in Cyber Security.
1. Malware.
2. Blame the User.
3. Reactive approaches to security will continue to fail.
4. Major Breaches in Sectors with Intellectual Property.
5. Hacktivists will bask in their new-found glory.
6. Critical Infrastructure Attacks.
7. Hello Android.
8. Windows Kernel Exploits.
9. Organized Crime rises.
10. Congress will rear its head.
Read full paragraph that goes with each of the above….
Phi Beta Iota: Nothing wrong with any of the above, except that they are out of context. As the still-valid cyber-threat slide created by Mitch Kabay in the 1990's shows, 70% of our losses have nothing to do with disgruntled or dishonest insiders, or external attacks including viruses. Cyber has not been defined, in part because the Human Intelligence crowd does not compute circuits, and the circuit crowd do not computer human intelligence. We are at the very beginning of a startling renaissance in cyber/Information Operations (IO) in which–we predict–existing and near-term hardware and software vulnerabilities will be less than 30% of the problem. Getting analog Cold War leaders into new mind-sets, and educating all hands toward sharing rather than hoarding, toward multinational rather than unilateral, will be key aspects of our progress. Cyber is life, life is cyber–it's all connected. Stove-piped “solutions” make it worse.
See Also:
Graphic: OODA Loop (Observe, Orient, Decide, Act)
Journal: 1 in 4 Fail US Army Extrance Exam
Journal: Development at Gunpoint? Wasteful & Wrong
Undersea Cables: The Achilles Heel of our Economies
U.S. Code-Cracking Agency Works As If Compromised. The U.S. government's main code-making and code-cracking agency now works on the assumption that foes may have pierced even the most sensitive national security computer networks under its guard.
“There's no such thing as ‘secure' any more,” Debora Plunkett of the National Security Agency said on Thursday amid U.S. anger and embarrassment over disclosure of sensitive diplomatic cables by the website WikiLeaks.
“The most sophisticated adversaries are going to go unnoticed on our networks,” she said.
Plunkett heads the NSA's Information Assurance Directorate, which is responsible for protecting national security information and networks from the foxhole to the White House.
“We have to build our systems on the assumption that adversaries will get in,” she told a cyber security forum sponsored by the Atlantic and Government Executive media organizations.
The United States can't put its trust “in different components of the system that might have already been violated,” Plunkett added in a rare public airing of NSA's view on the issue. “We have to, again, assume that all the components of our system are not safe, and make sure we're adjusting accordingly.”
The NSA must constantly fine tune its approach, she said, adding that there was no such thing as a “static state of security.”
More than 100 foreign intelligence organizations are trying to break into U.S. networks, Deputy Defense Secretary William Lynn wrote in the September/October issue of the journal Foreign Affairs. Some already have the capacity to disrupt U.S. information infrastructure, he said. Plunkett declined to comment on WikiLeaks, which has started releasing a cache of 250,000 diplomatic cables, including details of overseas installations that officials regard as vital to U.S. security.
Official have focused publicly on Army Private Bradley Manning, who is being detained at a Marine Corps base in Quantico, Virginia, as the source of the leak.
NSA, a secretive Defense Department arm that also intercepts foreign communications, conceives of the problem as maintaining the availability and assuring the integrity of the systems it guards, rather than their “security,” she said.
NSA – which insiders jokingly used to say referred to “No Such Agency” – also focuses on standardization and auditing to hunt for any intrusions, Plunkett said. She referred to the development of sensors for eventual deployment “in appropriate places within our infrastructure” to detect threats and take action against them.
Mike McConnell, a retired Navy vice admiral who headed the NSA from 1992 to 1996, told the forum he believed no U.S. government network was safe from penetration.
A third-party inspection of major computer systems found there was none of consequence “that is not penetrated by some adversary that allows the adversary, the outsider, to bleed all the information at will,” said McConnell, director of national intelligence from 2007 to 2009 and now leader of the intelligence business for the Booz Allen Hamilton consultancy.[Wolf/Reuters/18December2010]
Phi Beta Iota: In 1992 NSA knew that shrink-wrapped hardware and software coming across its loading dock was pre-compromised with both hardware and software viruses, Trojan Horse backdoors, and so on. In 1994 the National Information Infrastructure “leadership” refused to address the need for a $1 billion a year national cyber-security program. Since then it has simply gotten worse, with the latest (in the last four years) being the ability of the Chinese to ride the electrical circuits into any computer (think of your Best Buy ethernet extender that uses the wiring as a pass through). The good news is that 90% of what we have behind the green and black doors is not really secret or in such obscure minutia as to be immaterial to national security. What we should be doing, in our view as the proponent for public intelligence, is this:
1. Default both Whole of Government and Multinational Engagement to unclassified. Civil Affairs can lead the way with the Joint Civil Affairs Information Management Sytem that feeds the high side everything, but keeps the open system open.
2. Set a notional limit of 10% of what can be classified secret within any Embassy, roughly 8% for the spies and 2% for everyone else.
3. Take the most sensitive stuff completely off the electrical grid (the real reason NSA wants its own power station at Fort Meade and in Utah).
4. Invest one third of the cyber-war budget, whatever it ends up being (probably half), in education & research relevant to all stakeholders, not just the national security community. It is not possible to have smart safe spies within a dumb unsafe nation. It's all connected.
Turning away from secrecy is the single best thing we can do as a government, as a military, as a nation. It will yield productivity and innovation and foreign relations dividends beyond our dreams.
Everybody who's a real practitioner, and I'm sure you're not all naïve in this regard, realizes that there are two uses to which security classification is put: the legitimate desire to protect secrets, and the protection of bureaucratic turf. As a practitioner of the real world, it's about 90 bureaucratic turf; 10 legitimate protection of secrets as far as I am concerned.
Rodney McDaniel, then Executive Secretary of the National Security Council, to a Harvard University seminar, as cited in Thomas P. Croakley (ed), C3I: Issues of Command and Control (National Defense University, 1991). Page 68.


The FCC's Threat to Internet Freedom
‘Net neutrality' sounds nice, but the Web is working fine now. The new rules will inhibit investment, deter innovation and create a billable-hours bonanza for lawyers.
Tomorrow morning the Federal Communications Commission (FCC) will mark the winter solstice by taking an unprecedented step to expand government's reach into the Internet by attempting to regulate its inner workings. In doing so, the agency will circumvent Congress and disregard a recent court ruling.
Phi Beta Iota: The public is now much more aware that neither of the two political parties can be trusted, and that trust for any given government element, policy, or point of view is contingent on a much deeper examination of bias and motive than many would wish. There are two sides to this issue, irrespective of the competency and good faith of government: on the one side are the corporations, including Google and Verizon, that wish to hijack cyber-space and claim that they own it. This will allow them to charge premium prices for access to high-speed services. On the other are those whose taxes paid for the creation of the Internet in the first place, the US taxpayer–they see the vital importance of open spectrum, open source software, and open source intelligence as the tri-fecta of cyber-freedom. At OSS '92 John Perry Barlow said that the Internet interprets censorship as an outage, and routes around it. Our view is that the corporations will succeed in hijacking cyberspace in the near term, but in the mid-term and beyond OpenBTS and other bottom-up public innovation solutions will restore the noosphere to its rightful owners, the human minds that comprise the World Brain.