
There are numerous misleading and misinformed assertions being made about the defense spending parts of the debt deal.

There are numerous misleading and misinformed assertions being made about the defense spending parts of the debt deal.

Short URL: http://tinyurl.com/UNODIN
Steele in Dorn Peace from Above As Published
Finally published in 2014 (Article) originally presented in 2011 (Briefing).
The chapter more fully integrates the DNI spiral between modern mature intelligence (M4IS2) and modern mature Air Power.
Briefing 3.3 (29 Slides With Notes As Presented 40 KB pptx)
Event: 15-17 June Ontario UN Aerospace Power
See Also:
2012 Robert Steele: Practical Reflections on UN Intelligence + UN RECAP
UN Intelligence @ Phi Beta Iota
Worth a Look: Wings for Peace – First Book on Air Power in UN Operations
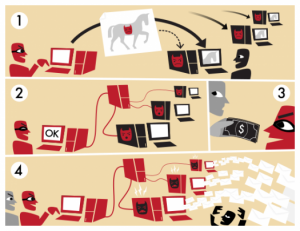
New Botnet, Now 4.5 Million Machines Strong, is ‘Practically Indestructible'
Today in cyber threats: more than four million Windows PCs have been commandeered by a botnet that cybersecurity experts are calling nearly “indestructible.” Known as TDL-4 (it’s the fourth iteration of the malicious program), this particular little nuisance hides in places security software rarely checks and speaks with other infected machines and their overseers in a novel encrypted code. Some are calling it the most sophisticated threat out there today. Watch your back, Stuxnet.
Phi Beta Iota: Apart from the known fact that the US Government ignored documented warning from Winn Schwartau, Jim Anderson, Bill Caelli, and Robert Steele in 1994, what we have here is the culimination of fifteen years in which governments continue to operate as Industrial Era hierarchies, choosing secrecy to protect incompetence rather than multinational sharing to achieve resilience–they are as a result inept beyond belief. The cloud–given the plethora of proprietary and therefore generally insecure hardware and software–is not going to be cleaned up on the present course, where spam is 75% of all email despite the best (isolated) efforts of all concerned. M4IS2, anyone?
Journal: Army Industrial-Era Network Security + Cyber-Security RECAP (Links to Past Posts)
Industrial productivity can be achieved on a small scale….it just requires open source design. A single DVD is a civilization starter kit.
Using wikis and digital fabrication tools, TED Fellow Marcin Jakubowski is open-sourcing the blueprints for 50 farm machines, allowing anyone to build their own tractor or harvester from scratch. And that's only the first step in a project to write an instruction set for an entire self-sustaining village (starting cost: $10,000).

There are a set of documents at the DOT&E website which offer DOT&E insights into the reason for why about 40 programs have experienced delays — and costs. These documents relate to a Tony Capaccio story in today's Bloomberg News (below).
The document titled “Updated DOT&E Input on Program Delays” (at the DOT&E link shown above) identifies various specific reasons for the problems programs experience — different from most of the explanations from contractors and other system advocates in and out of the Pentagon. (Eg. for the F-35: Fly rates per month lowered to more realistic projections (from 12 max for all variants and venues to 10 max for CTOL/CV flight sciences, 9 max for STOVL flight sciences, 8 max for all mission systems); increased planning factors for re-fly and regression (up 15% for flight science, 10% for mission systems); more time required for software development and incremental builds.”)
Beyond the F-35, the various systems described in the analysis are typically more obscure programs (eg. AIM-9X 8.212 Software Upgrade) but there are also a few better known ones, such as LCS, which is described in “fly before buy,” Congress and the Navy want to rush ahead of testing to buy 4 LCS in the 2012 HASC DOD Authorization bill for $1.8 billion in production costs.
Availability of complete mission packages will be delayed until at least 2015.
Instead of withholding production of untested systems with clear and obvious development problems, Congress and the Pentagon are intent on business as usual. The LCS is a good example: instead of “fly before buy,” Congress and the Navy want to rush ahead of testing to buy 4 LCS in the 2012 HASC DOD Authorization bill for $1.8 billion in production costs.
Some will think the DOT&E analysis and documents to be obscure and too “in the weeds” to pay much attention to. Instead, they offer a major part of the explanation for why hardware costs and delays are so out of control, and they offer a stunning view into how little is being done about that.
BloombergNews.com, June 13, 2011

Phi Beta Iota: The industrialization/ chemicalization of agriculture, in combination with the corruption of every aspect of society beginning with governance and extending to the media, has allowed for the desecration of the Earth and the poisoning of humanity. This has been done with the explicit consent and encouragement of the so-called elites of the West, who have a vision of eugenics and the covert eradication of the poor and uneducated over time. These elites do not see that the brainpower of the three billion poor is the only thing that can restore natural harmony and sustainable agriculture as well as legitimate governance and natural capitalism. The time has come to create M4IS2–public intelligence in the public interest.
Analysis: In “borderless” cyberspace, nation states struggle
By Peter Apps, Political Risk Correspondent
Reuters LONDON | Thu Jun 9, 2011
EXTRACT:
“The nature of cyberspace is borderless and anonymous,” R. Chandrasekhara, secretary of India's telecommunications department, told a cyber security conference in London last week organised by a U.S.-based think tank, the EastWest Institute. “Governments, countries and law — all are linked to territory. There is a fundamental contradiction.”
Tip of the Hat to Chris Pallaris at LinkedIn.
Phi Beta Iota: The national secret intelligence communities mean well, but they are cognitively and culturally incapacitated in relation to both the global threats and the global infomation sharing and sense-making possibilities. It may just be that the solution has to come from a private sector service of common concern that can provide the integrity now lacking in governments and most corporation. Scary thought. M4IS2 is inevitable….delay is costing trillions.